

Allows to see
virus from the inside
The tLab system is an advanced Anti-APT product for protection against a new type of cyber threat: against zero-day attacks, targeted malicious software (malware) and APT attacks

Autonomy
Our system automates anti-malware protection by integrating seamlessly with your existing Mail / Web Gateway components and other third-party solutions using REST API and standard protocols
Intellectuality
Deep analysis of malicious behavior and heuristic analysis, which ensure the recognition of complex and hidden malware attacks
Perfomance
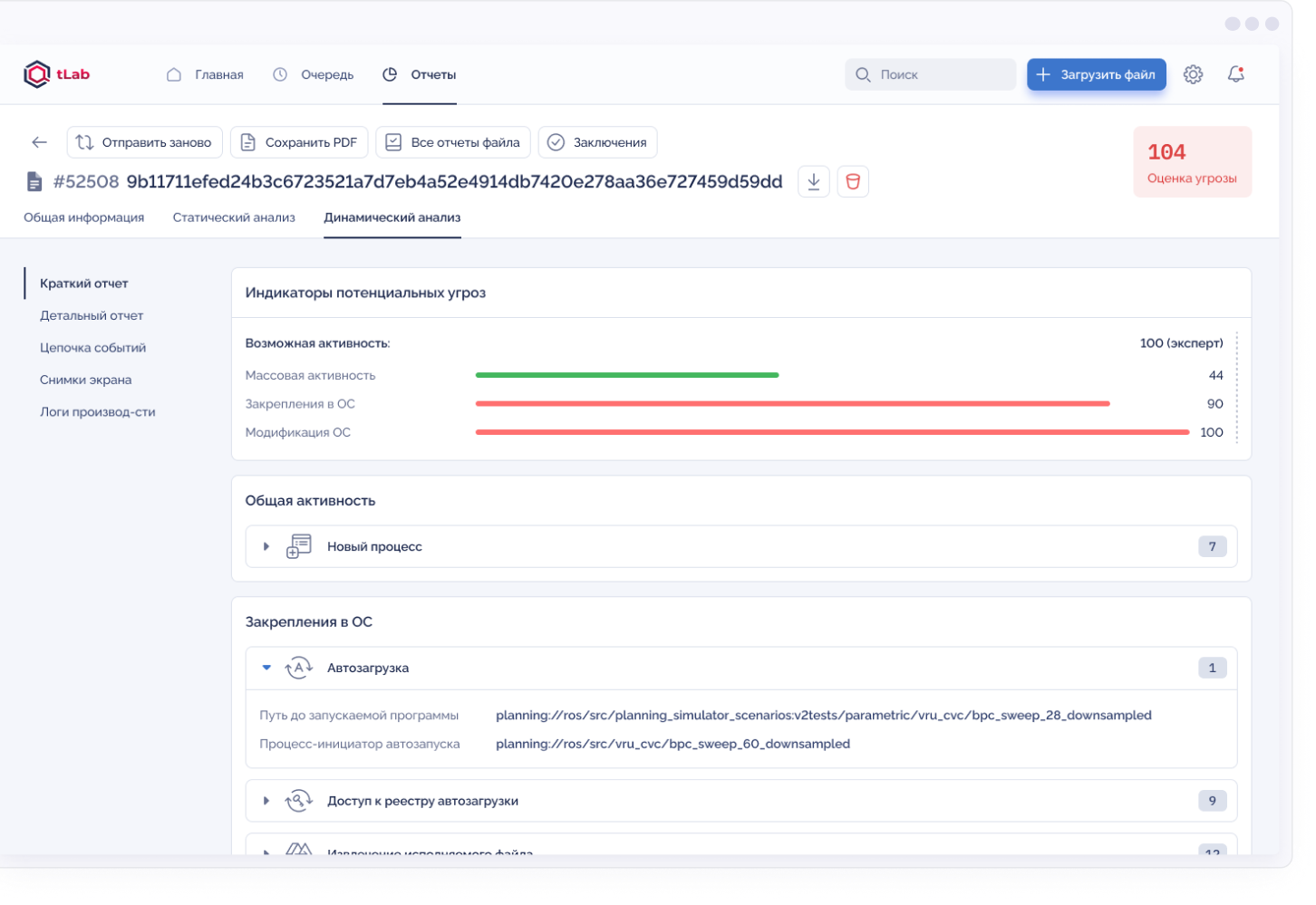
Quick assessment of the malware threat based on a comprehensive, interactive report that allows you to view the threat from the inside

Detects over 100 types of malicious activity

Checks up to 10,000 viruses per day (on one server)

Allows you to get a verdict on an object in 60 seconds

Based on more than 10 scientific papers from the USA

Advantages
for client
Advanced attack detection
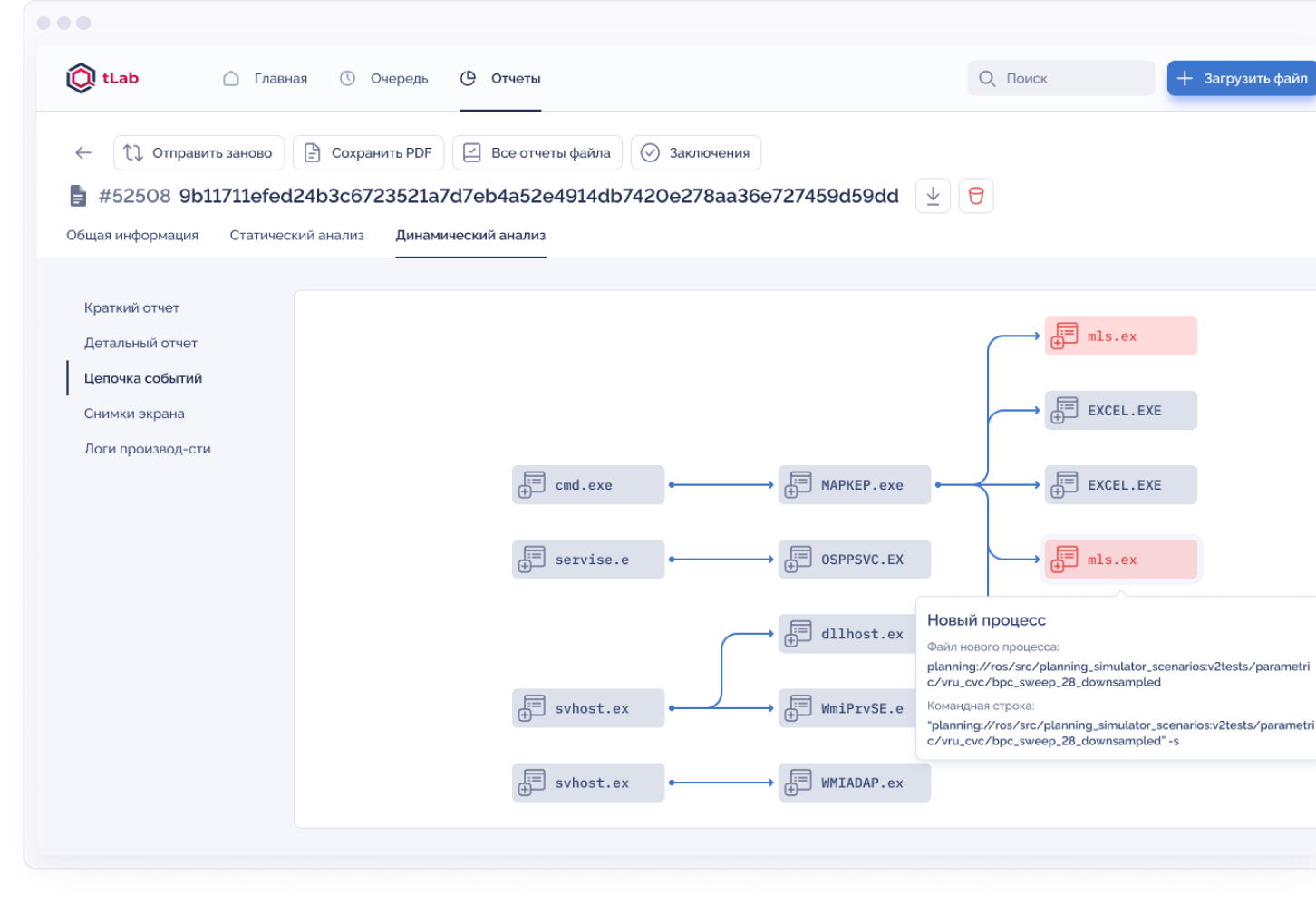
tLab identifies malware by in-depth analysis of the system behavior of programs in an isolated environment. A unique technology is used for analyzing behavior at the level of activity trees, which describe the flow of propagation of malicious activity and the relationship of executable objects. This technology allows detecting hidden and complex malicious objects that are hardly noticeable for traditional protection systems.
tLab analyzes many file formats for malware, including but not limited to: documents, scripts, web files, executables, archives, etc. client application files (eml).
tLab analyzes many file formats for malware, including but not limited to: documents, scripts, web files, executables, archives, etc. client application files (eml).

Defence
against hidden attacks
Advanced User Activity Emulation (VPO Detonation)
Some types of unwanted and malicious software require interaction with the user, accordingly, such samples will not be activated (detonated) until the user clicks on the corresponding elements of the graphical interface (buttons, text fields). Such threats include Trojan programs masquerading as legitimate software or unwanted software that requires a complete installation script. Also, ransomware trojans may require interaction with the user to perform some operations, for example, contacting the attacker's server to download information on ransom payments. Detonating such VPO objects requires an advanced and efficient user emulation system as a level.
Some HSV samples show the user a static graphic image to bypass sandboxes and do not use system controls, tracking the user's click on the button picture. Sandboxes cannot recognize the controls and, accordingly, cannot press and detonate the GRT. tLab includes a pattern recognition module for identifying elements
Some HSV samples show the user a static graphic image to bypass sandboxes and do not use system controls, tracking the user's click on the button picture. Sandboxes cannot recognize the controls and, accordingly, cannot press and detonate the GRT. tLab includes a pattern recognition module for identifying elements
Detailed threat research
Unlike classic sandboxes, tLab not only detects and blocks attacks in real time, but also provides powerful tools for comprehensive threat research. tLab, identifies the malware threat level and provides an interactive report with visualization of full activity and an indication of malicious functions.
Anti-evasion
mode
mode
tLab has the ability to counteract known sandbox detection and traversal techniques, including: analysis environment artifact detection, deferred execution, and an advanced approach using micro-latency loops. This technology of countering sandbox circumvention determines the effectiveness in detecting covert targeted and atypical attacks, which, according to world practice, form the basis of the modern malware threat model.
