Analysis of the Rising Sun backdoor by APT Lazarus in the tLab system


In December 2018, McAfee released a report on a large malware campaign targeting the financial, energy and other sectors of the economy, called Operation Sharpshooter. The North Korean APT group Lazarus is responsible for the numerous attacks. Operation Sharpshooter began on October 25, 2018 with the distribution of malicious Microsoft Word documents through the Dropbox service. The documents contained a malicious macro that injected the loader into the memory of the Microsoft Word process. Further, the downloader received a malicious file with basic functionality from the attackers' servers. McAfee gave it the name Rising Sun.
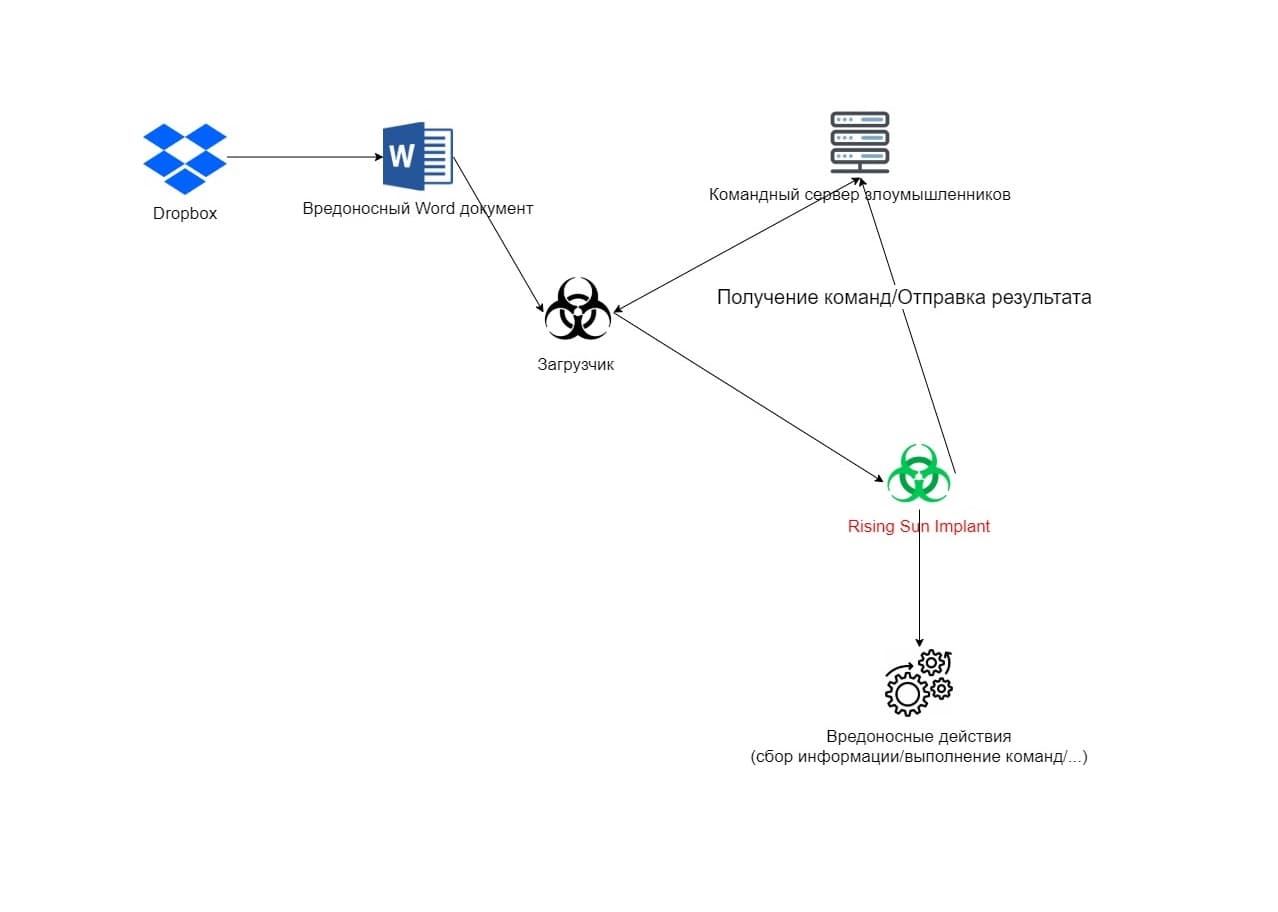
In contrast to the already known data in the McAfee report, we will try to show the Rising Sun in action (dynamically) and talk about how you can dynamically analyze malicious files in the absence of working C&C servers. The sample under study has the following hash sums:
MD5: 2e17b048c7e317da9024a86d9439c74bSHA1: 31e79093d452426247a56ca0eff860b0ecc86009SHA256: 37b04dcdcfdcaa885df0f392524db7ae7b73806ad8a8e76fbc6a2df4db064e71
SHA512:
7ee51e53242e59f49d32d6344cbb2c9f2976c7787d00b63d2470c83ff3053b83c86b37b2870127934e60001ed39cb99f486e07a900d34e5a6ba8d240e233494b
Creating an implant for the Rising Sun
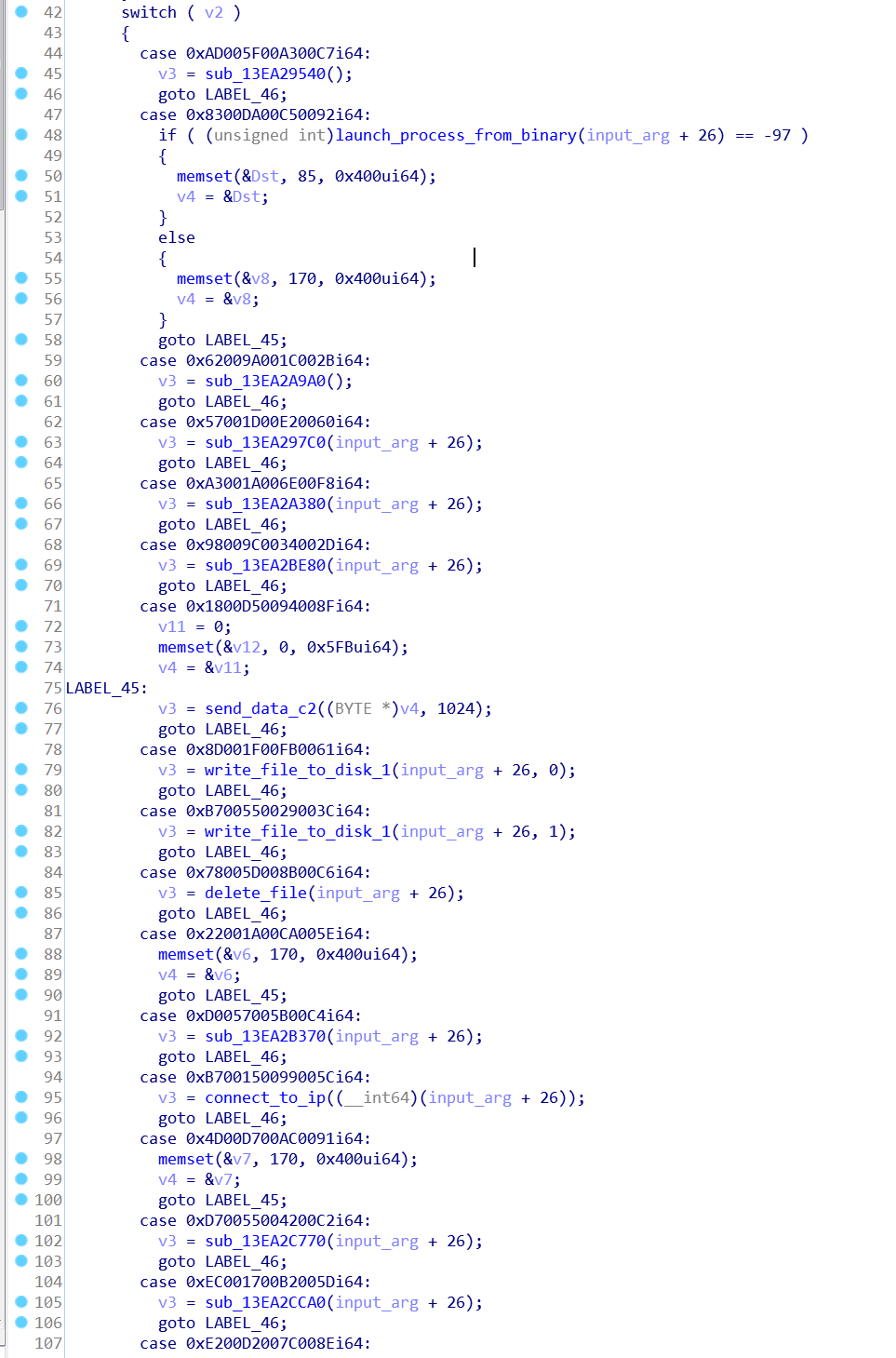
The Rising Sun receives RC4-encrypted commands from the attackers' servers, executes and sends the result. Depending on the command, one or another malicious action is performed (reading a file, starting a process, collecting information, etc.). Commands are strictly defined constants. The main function that processes commands from the server:
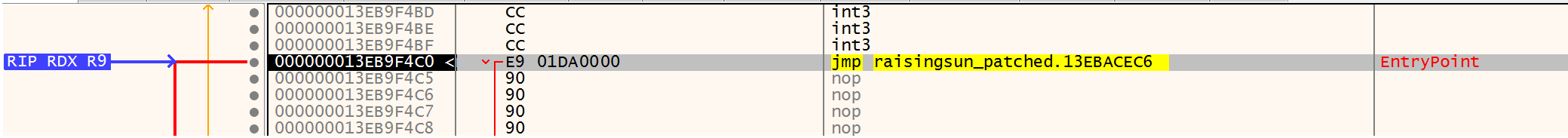
Since the servers are no longer available, to test the functionality, we developed an implant for the sample under study, for testing in the tLab sandbox. The implant allows the sample to receive commands from the command line, instead of C&C servers, and perform original malicious actions. To begin with, the entry point was modified to make the transition to the implant code:
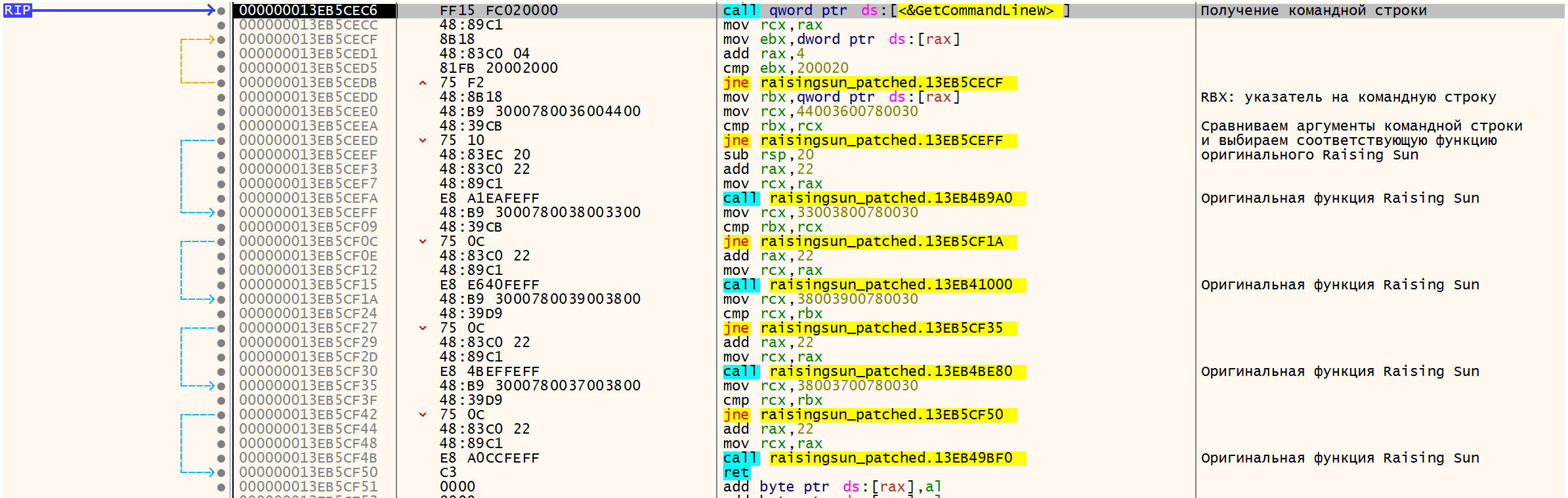
The implant receives the command line and, by the first argument, determines which function should be called:
Command line example:
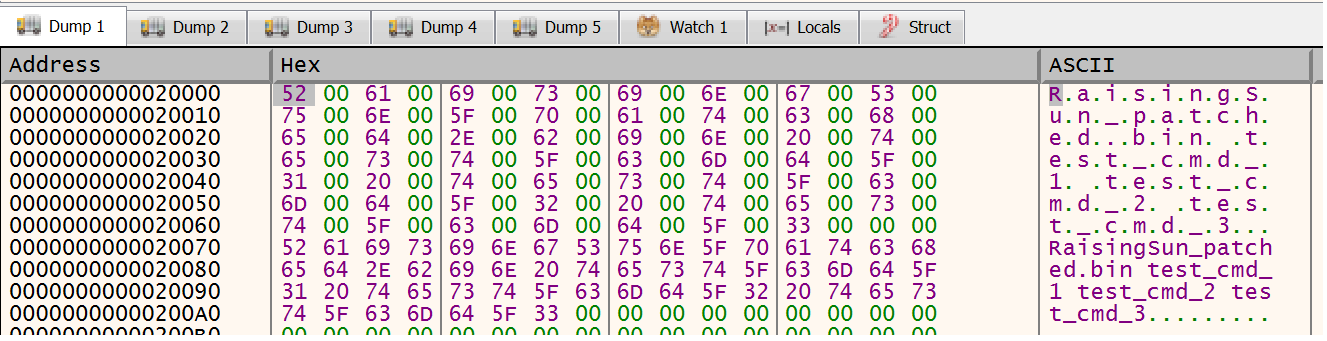
Analysis of the Rising Sun in the tLab system
The sample under research is intended for 64-bit systems, so the appropriate configuration was chosen in the tLab system:
tLab successfully identified Rising Sun as malware, rating it as high threat level based on static and dynamic analyzes. The hash sums are different because the sample we modified was used.
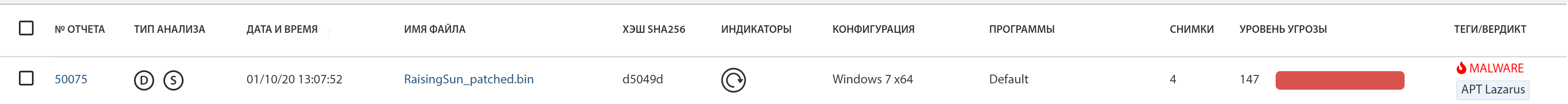
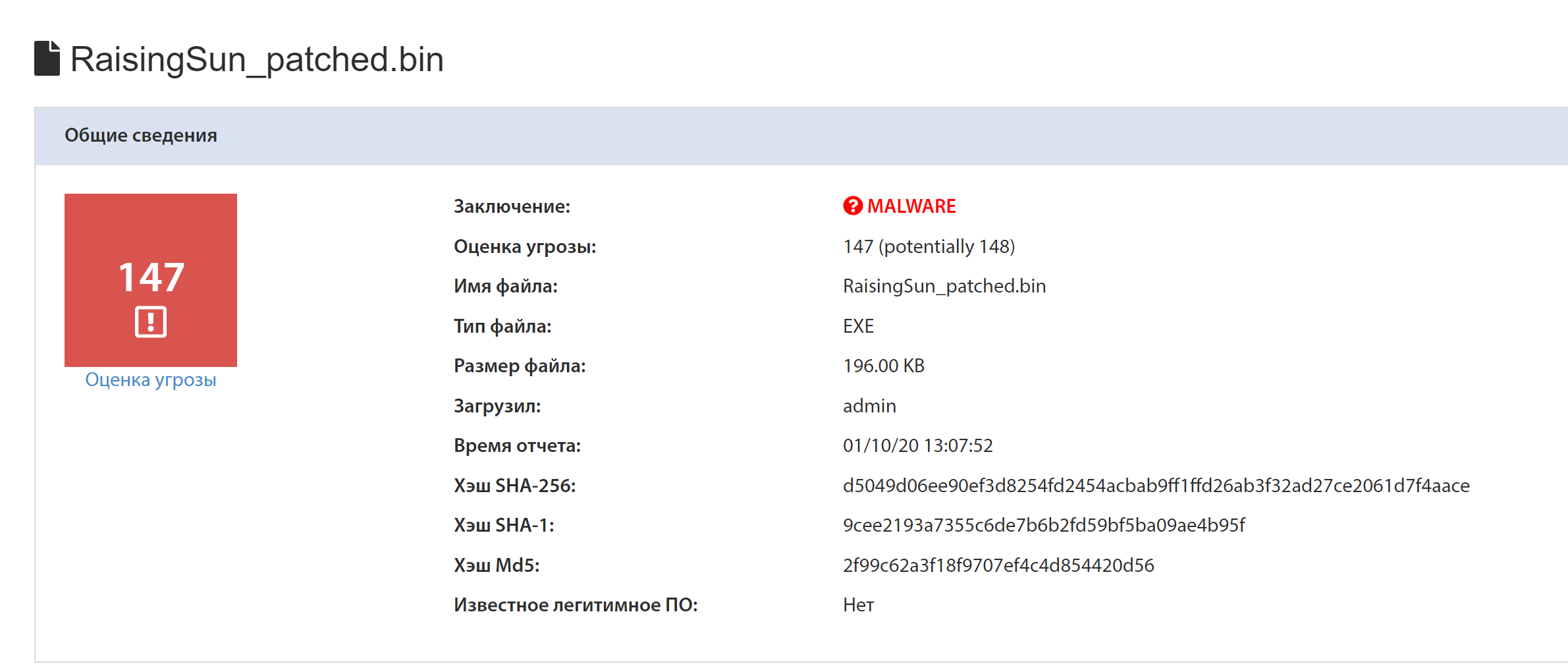 General information about the report
General information about the report
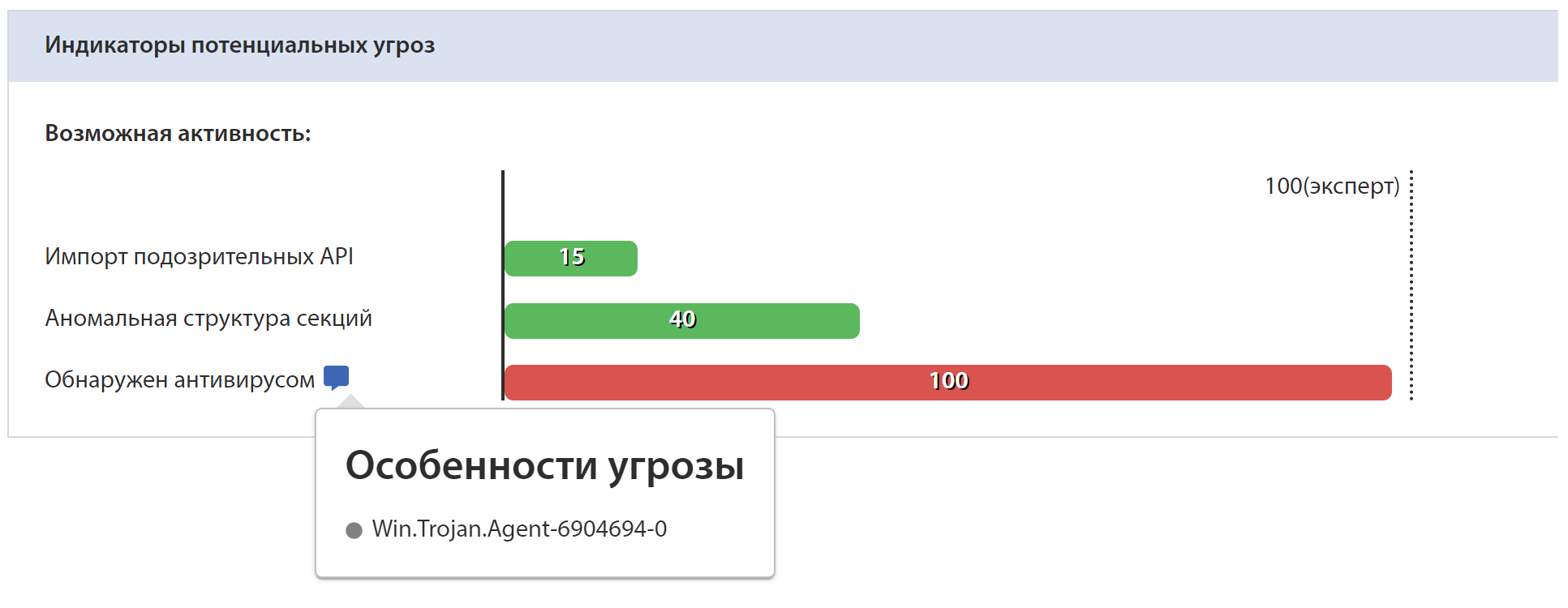 Static analysis
Static analysis
Rising Sun communicates with the server in encrypted form. The encryption method can be determined by the lines in the malicious file:
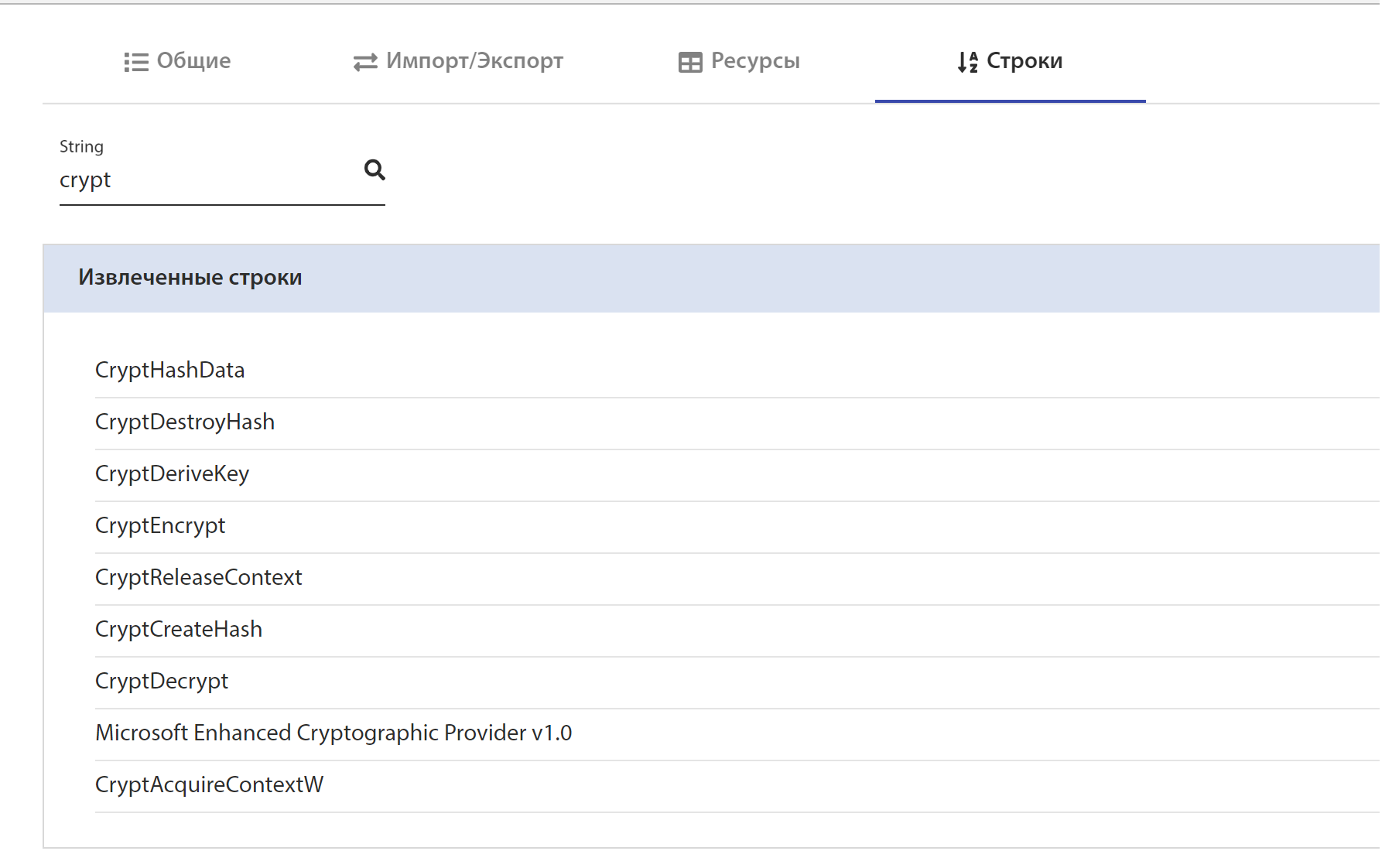
Rising Sun: Command Line Execution
Now let's move on to demonstrating the functionality. Let's start with the function to run a command on the command line, obtained from the server:
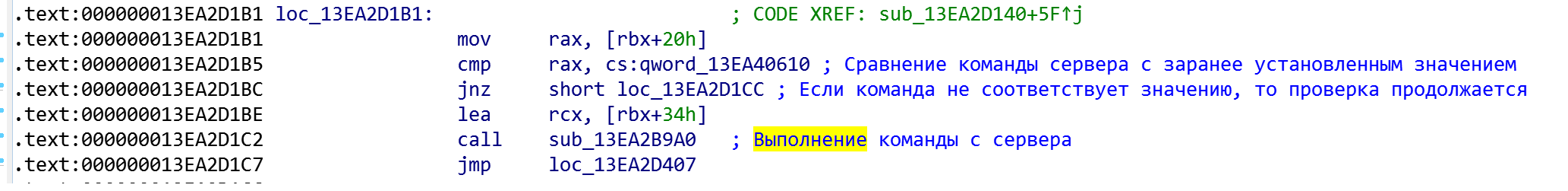
Constant for the command - 0x6D0017005500F7
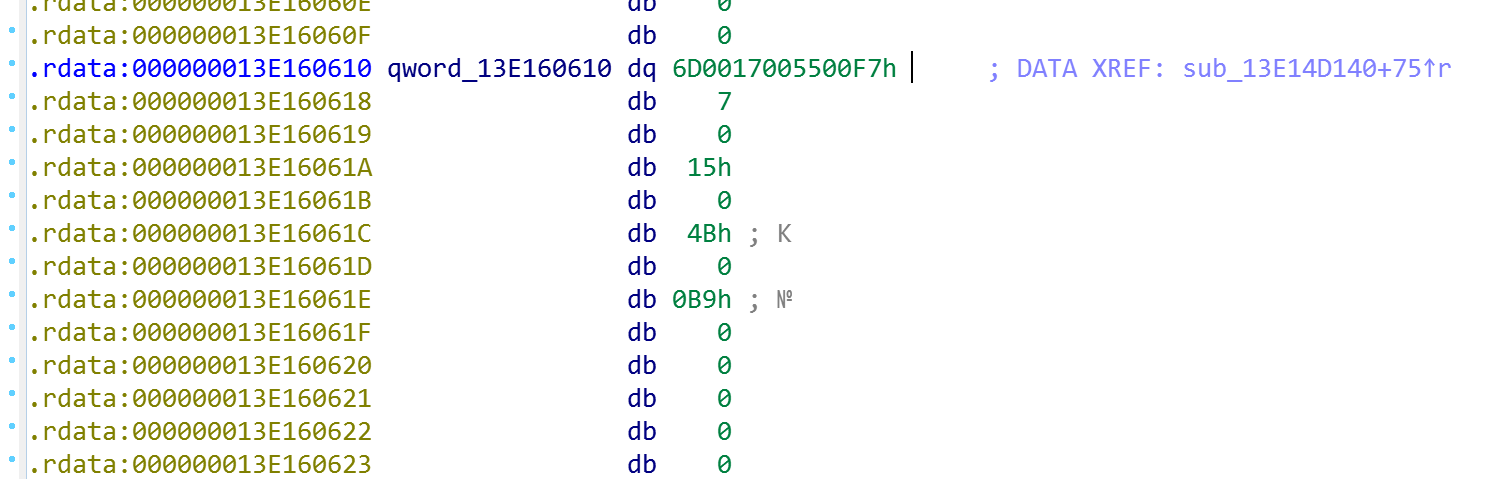
Function sub_13EA2B9A0, a temporary file is created to record the result of the command:
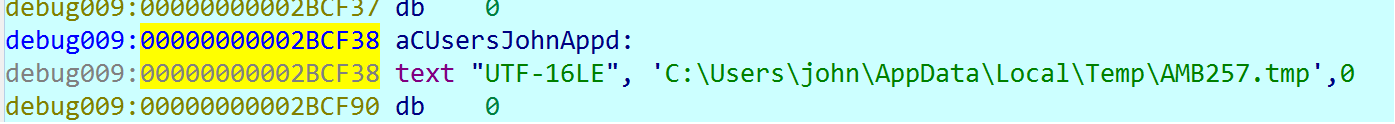
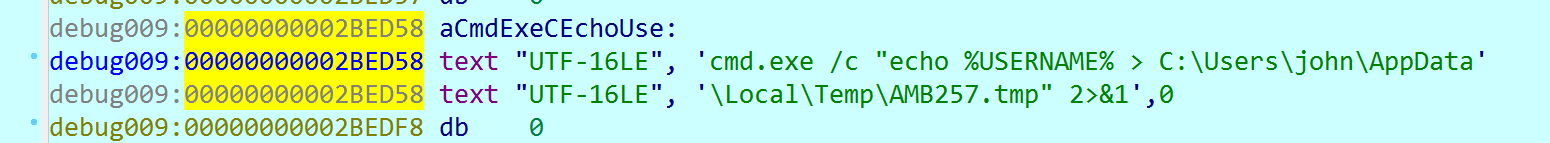
Next, the Rising Sun generates a command line like this:
For demonstration in this case, we passed the echo% USERNAME% command, which displays the name of the current user
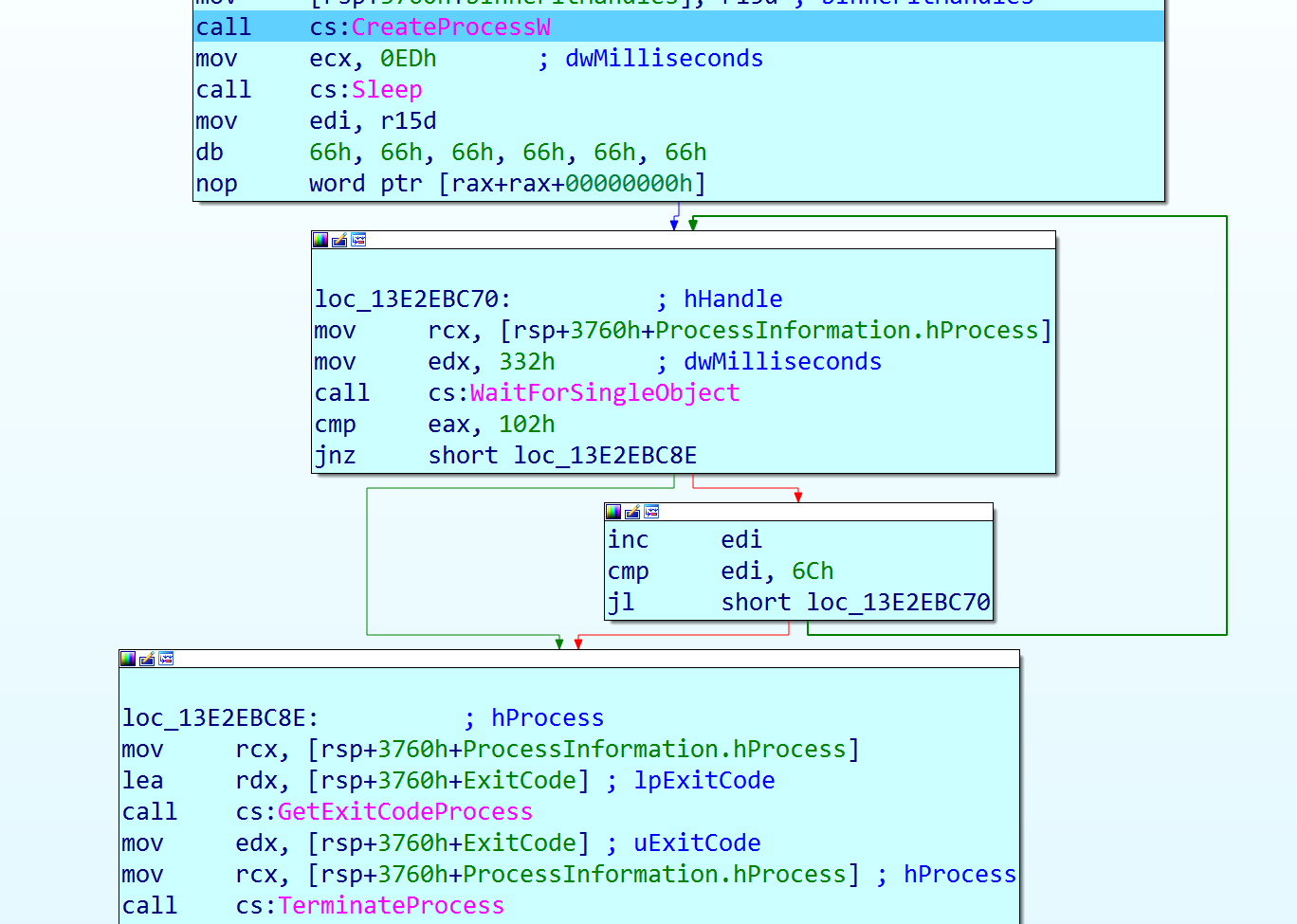
The command line is executed by calling CreateProcess ():
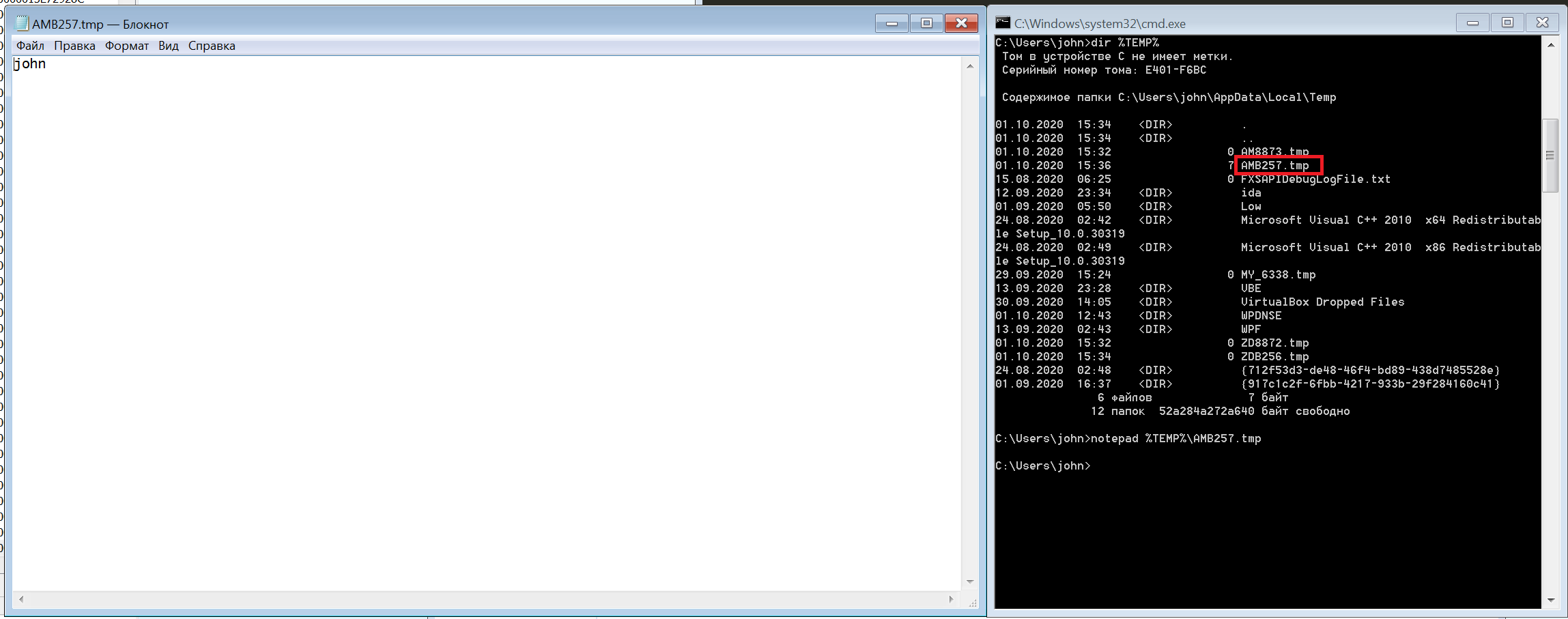
As a result, the temporary file contains the output of the executed command (which is immediately sent to the attackers' server):
Let's look at a more real-world example: getting a command from the server to install Rising Sun as a service. tLab determined the fact of fixing the OS:
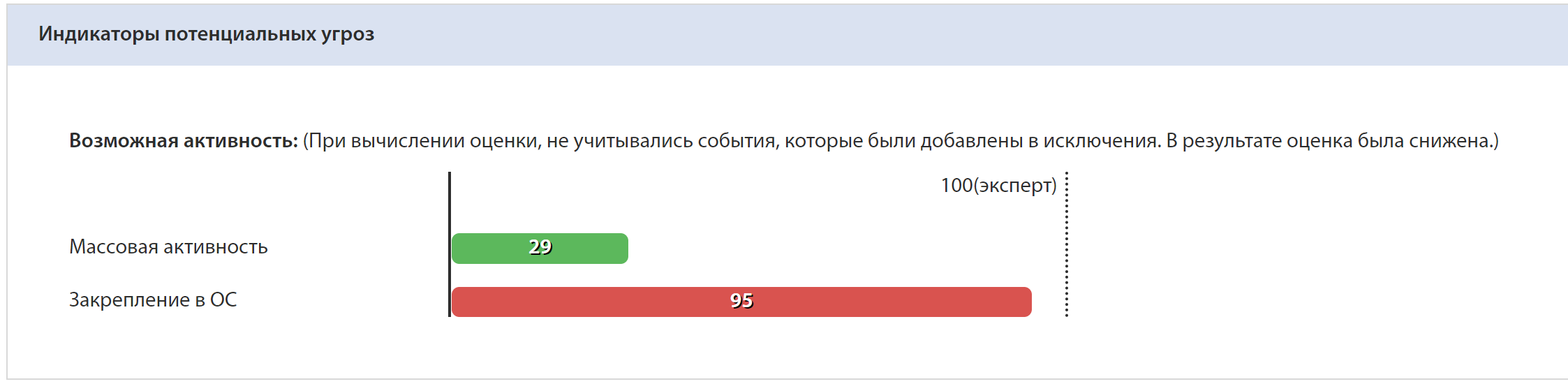
Among the list of created processes, you can see sc.exe:
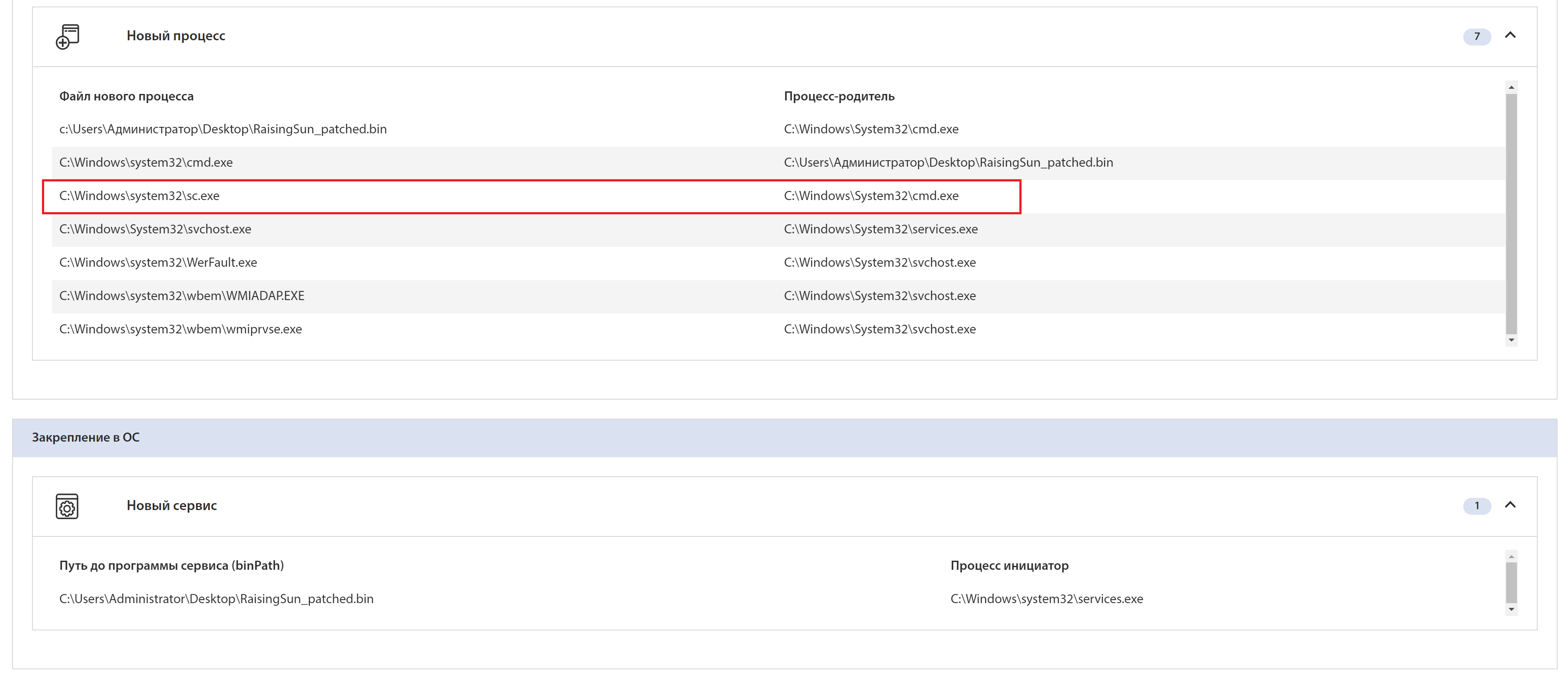
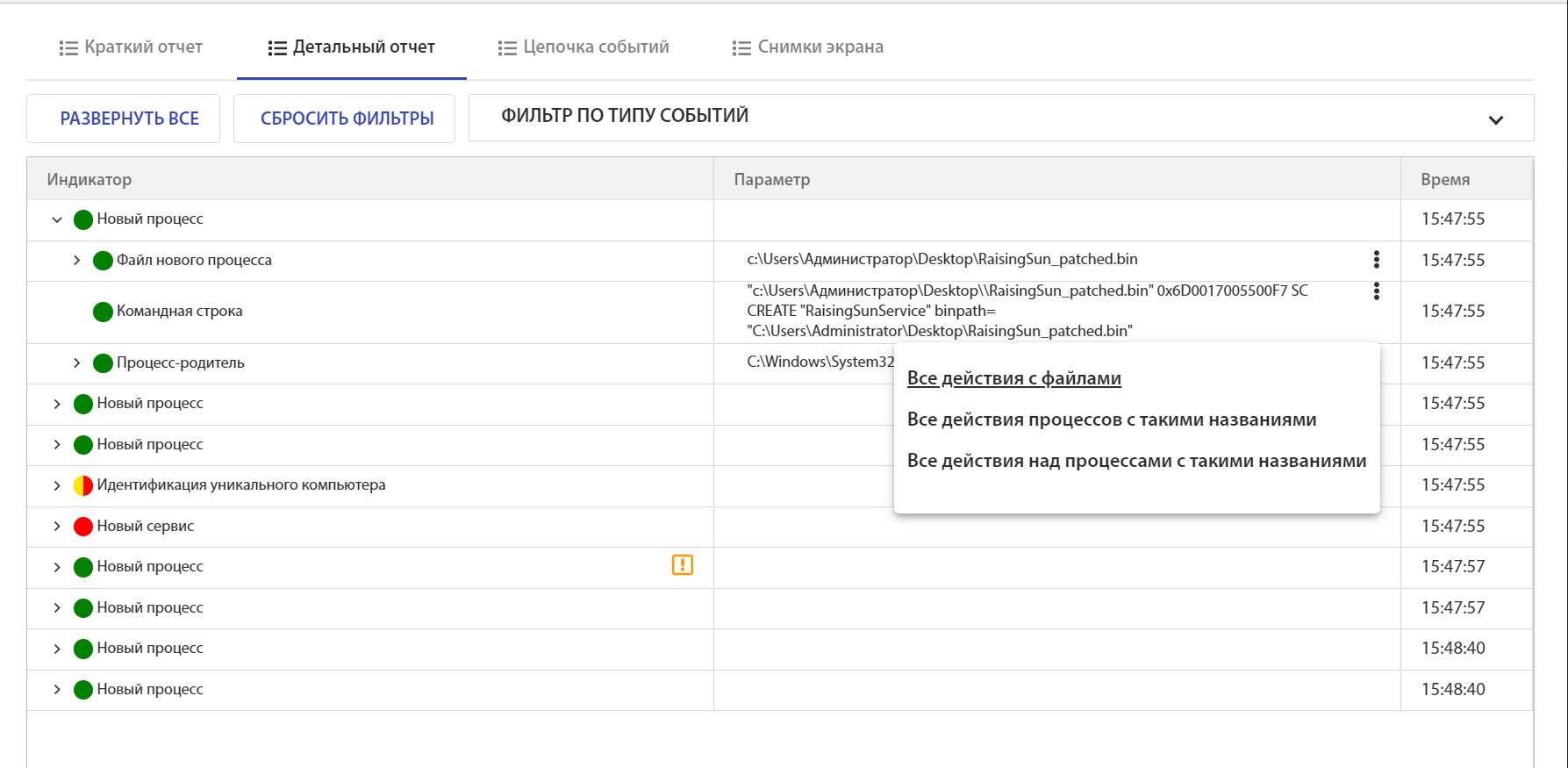
You can see all the actions associated with a specific file:
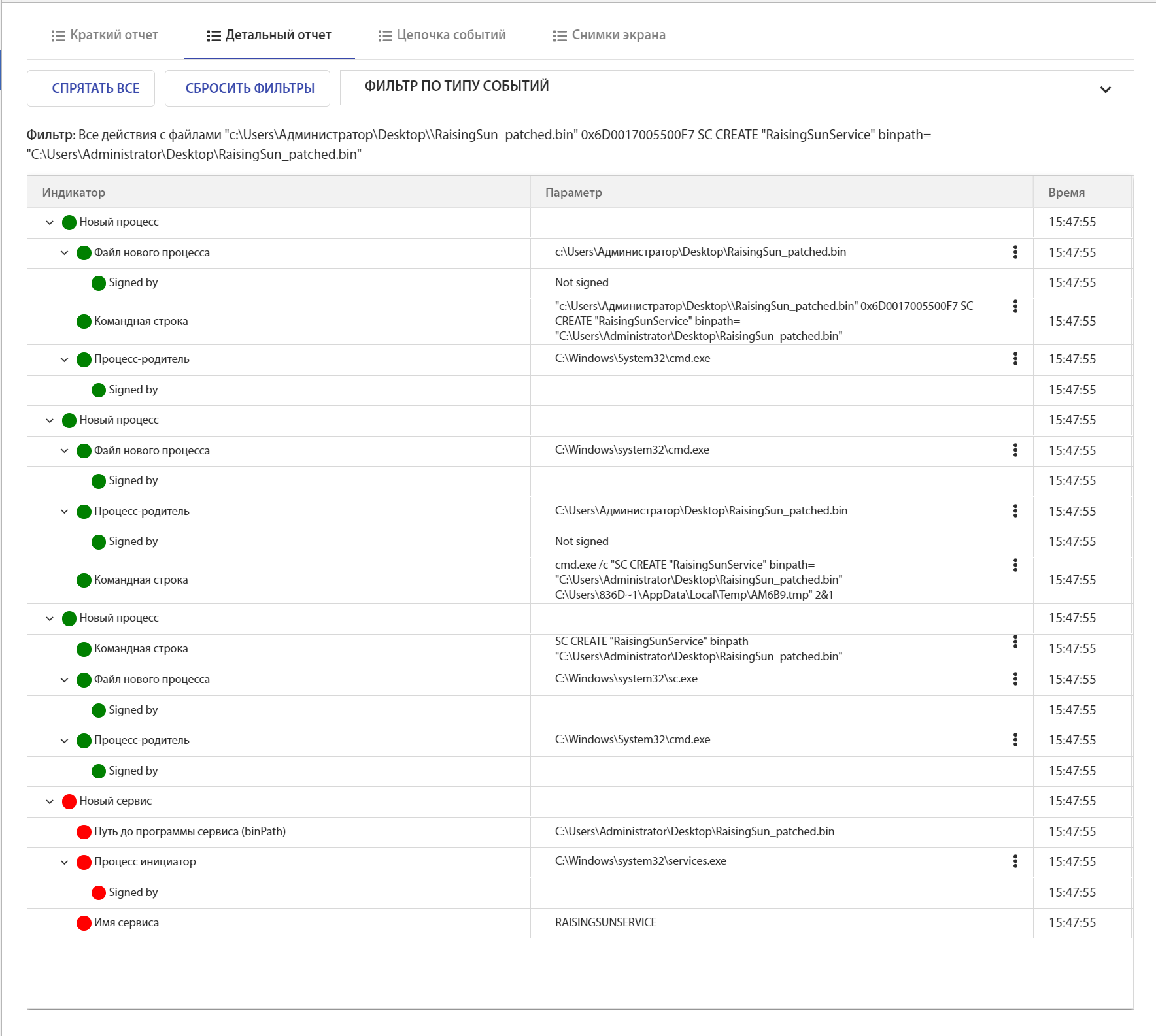
In the "Chain of events" you can clearly see the created service "Rising Sun":
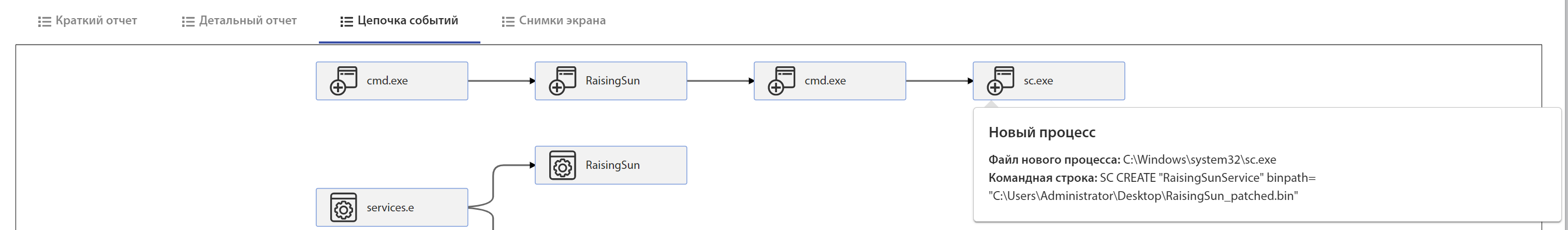
Rising Sun: Run the executable
The constant for this command is 0x8300DA00C50092:
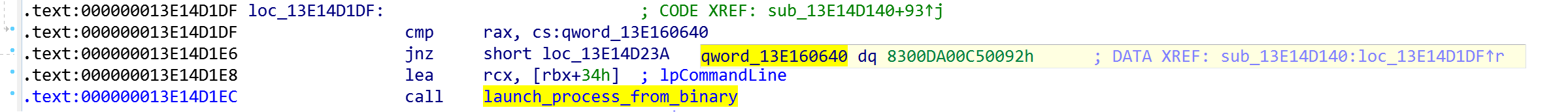
Launching is done by calling CreateProcess (). Launch example:
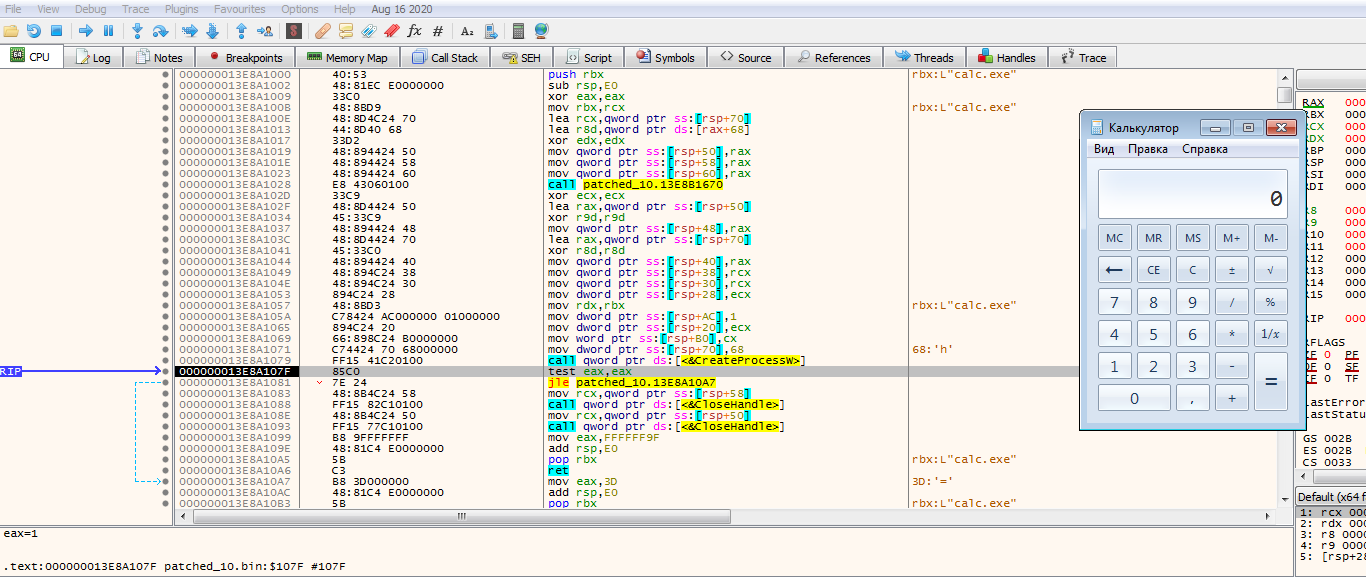
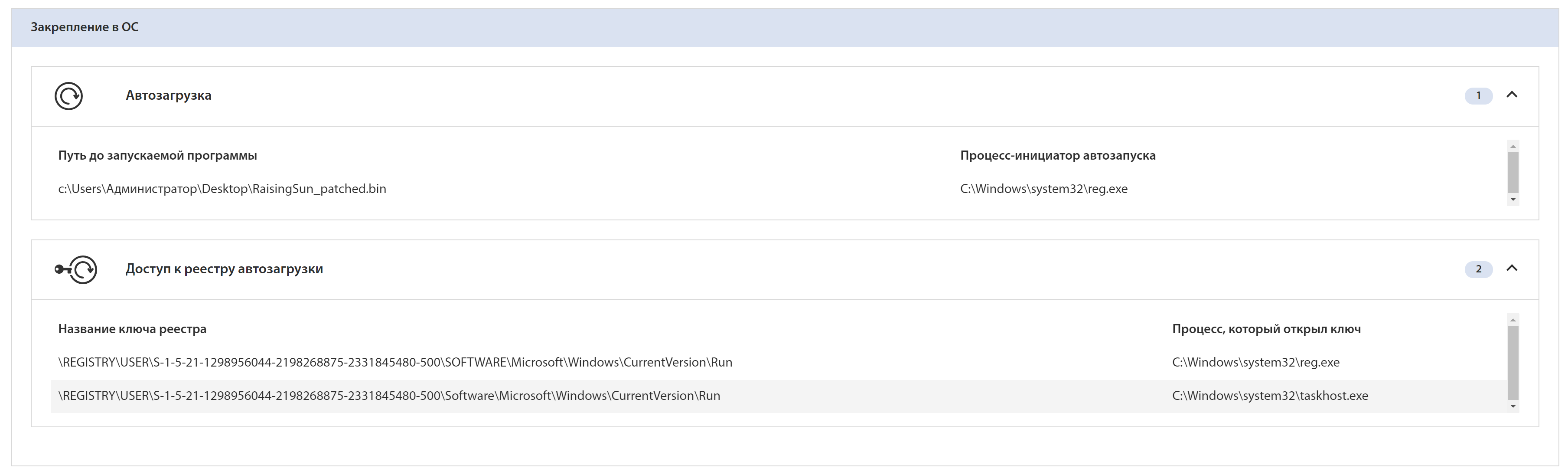
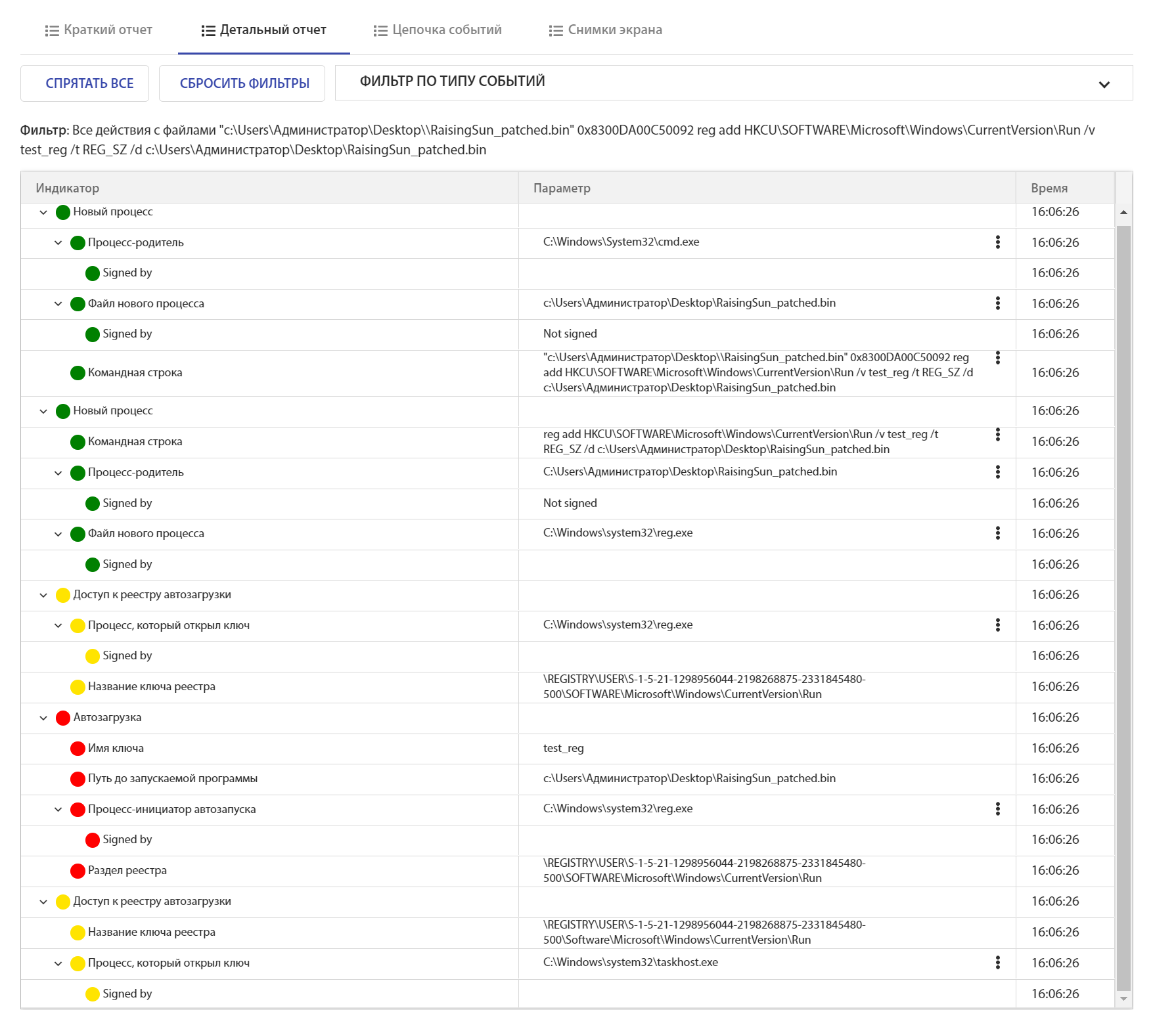
On the tLab system, Rising Sun was launched with the reg.exe launch command and adding itself to autorun:
0x8300DA00C50092 reg add HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run /v test_reg /t
REG_SZ /d c:\Users\Администратор\Desktop\RaisingSun_patched.bin
tLab has defined an addition to autoload:
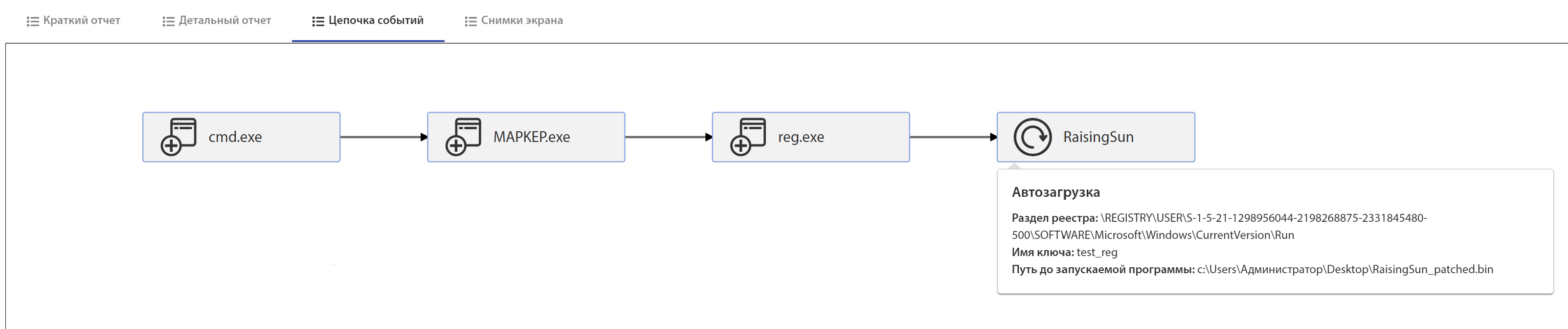 Common execution chain
Common execution chain
Rising Sun: Reading Files
The constant for the command is 0x98009C0034002D
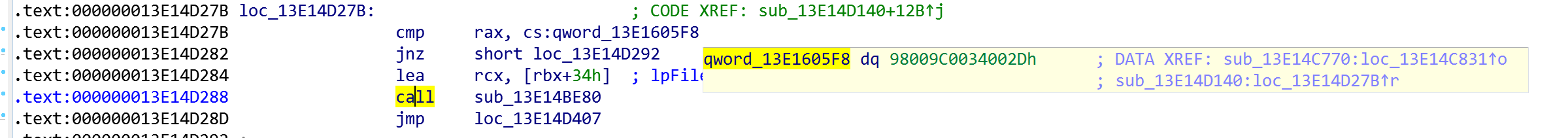
Rising Sun was launched with the command to read a user file:
0x98009C0034002D C:\\Users\\Администратор\\Desktop\\1_Ico.png
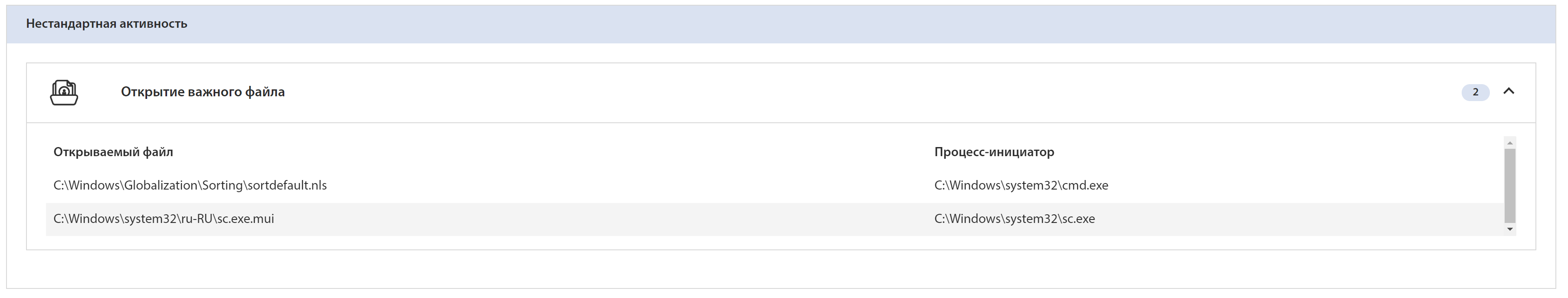
tLab detected a suspicious file opening:
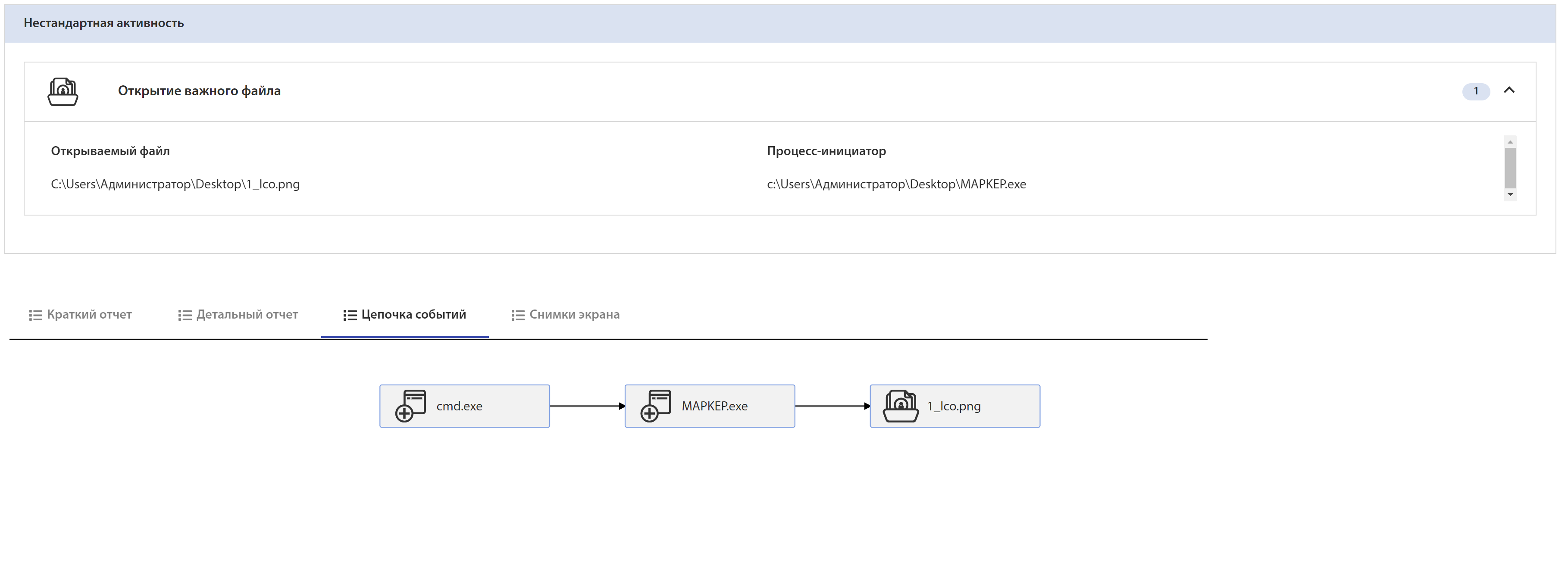
tLab can show a list of actions for a specific file:
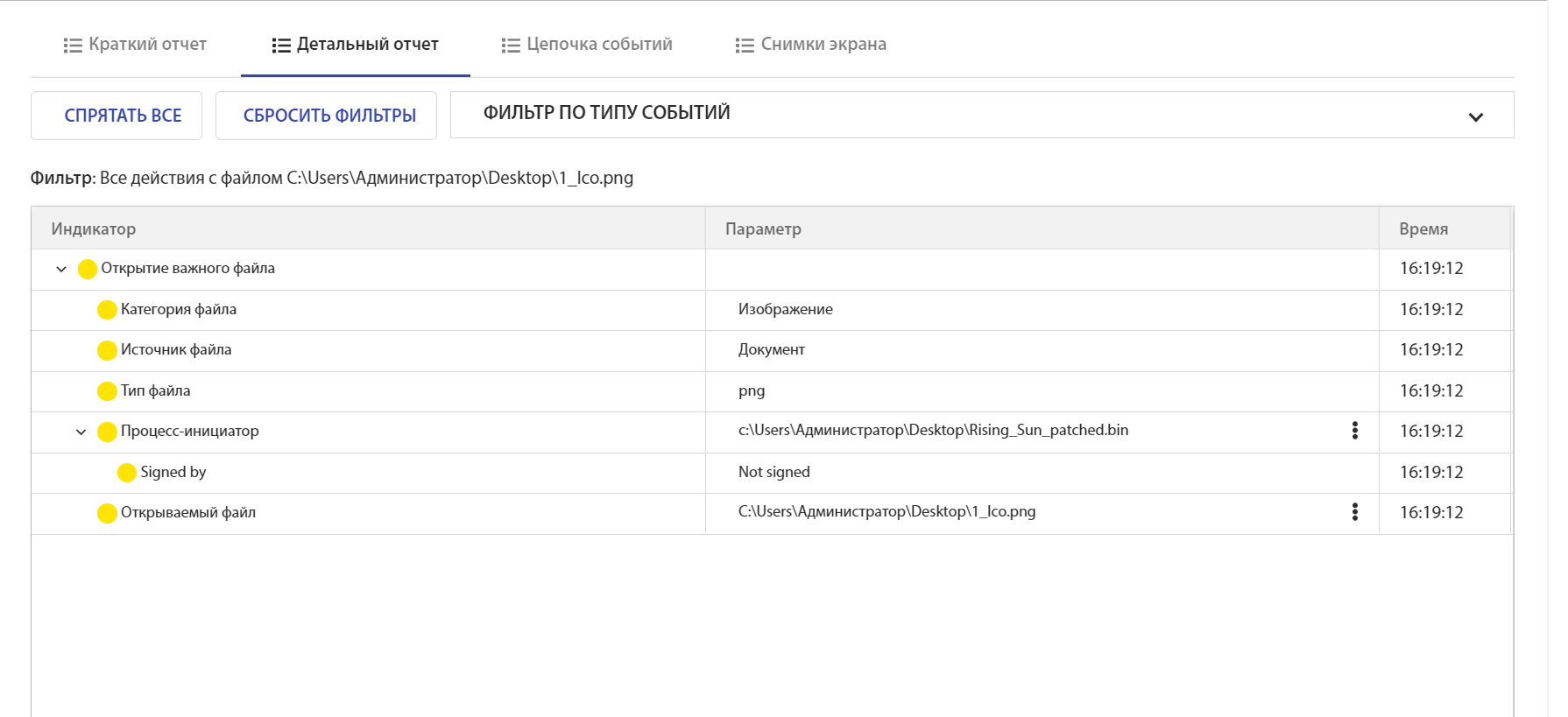
Rising Sun: Deleting Files
The constant for the command is 0x78005D008B00C6
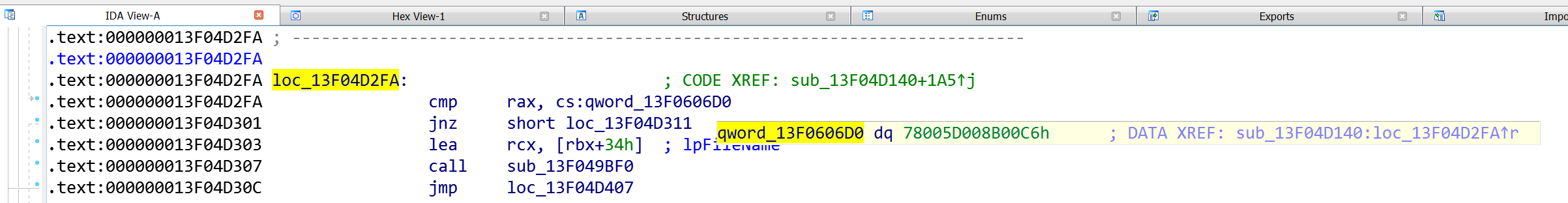
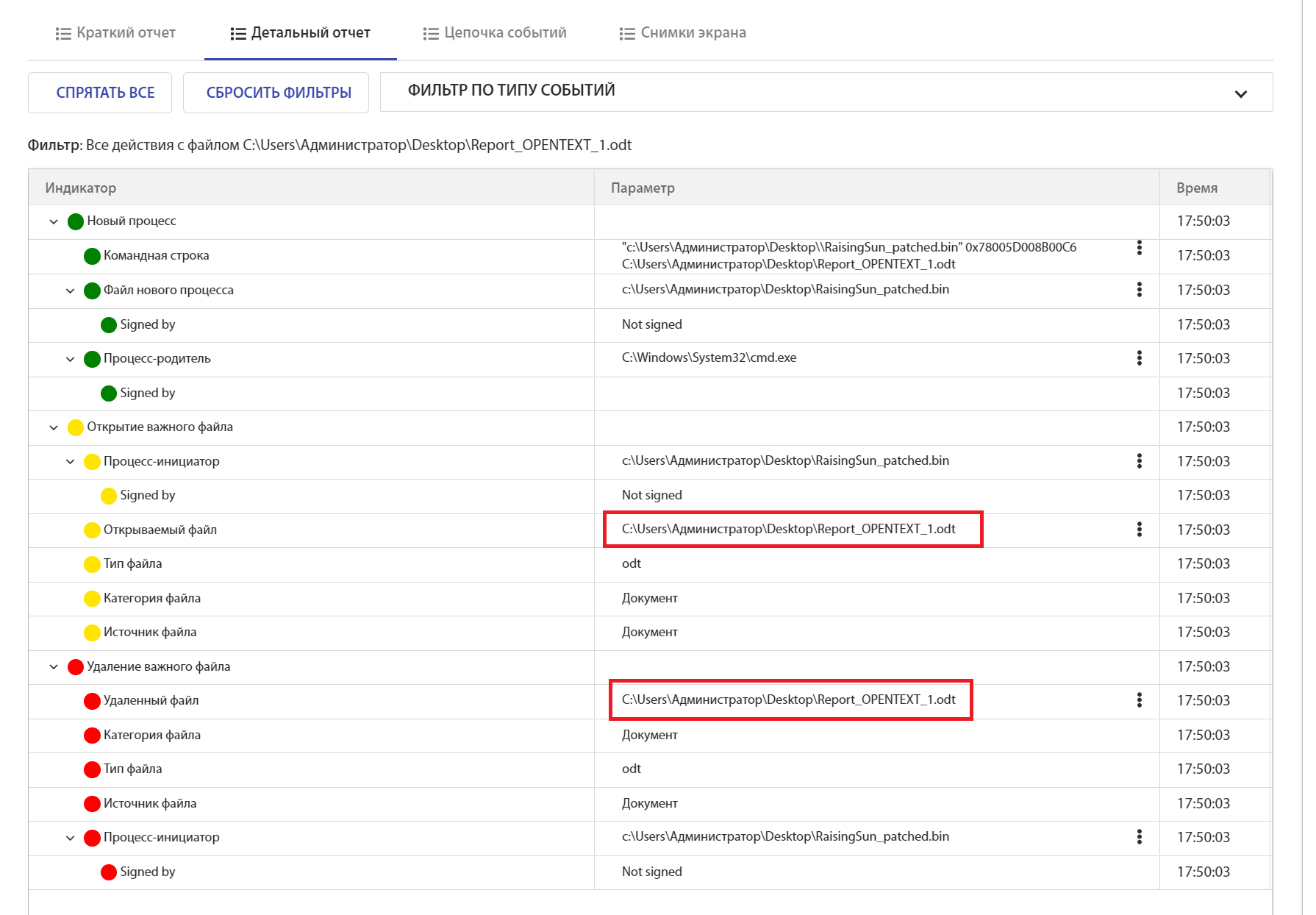
Rising Sun was launched with the command to delete a user file:
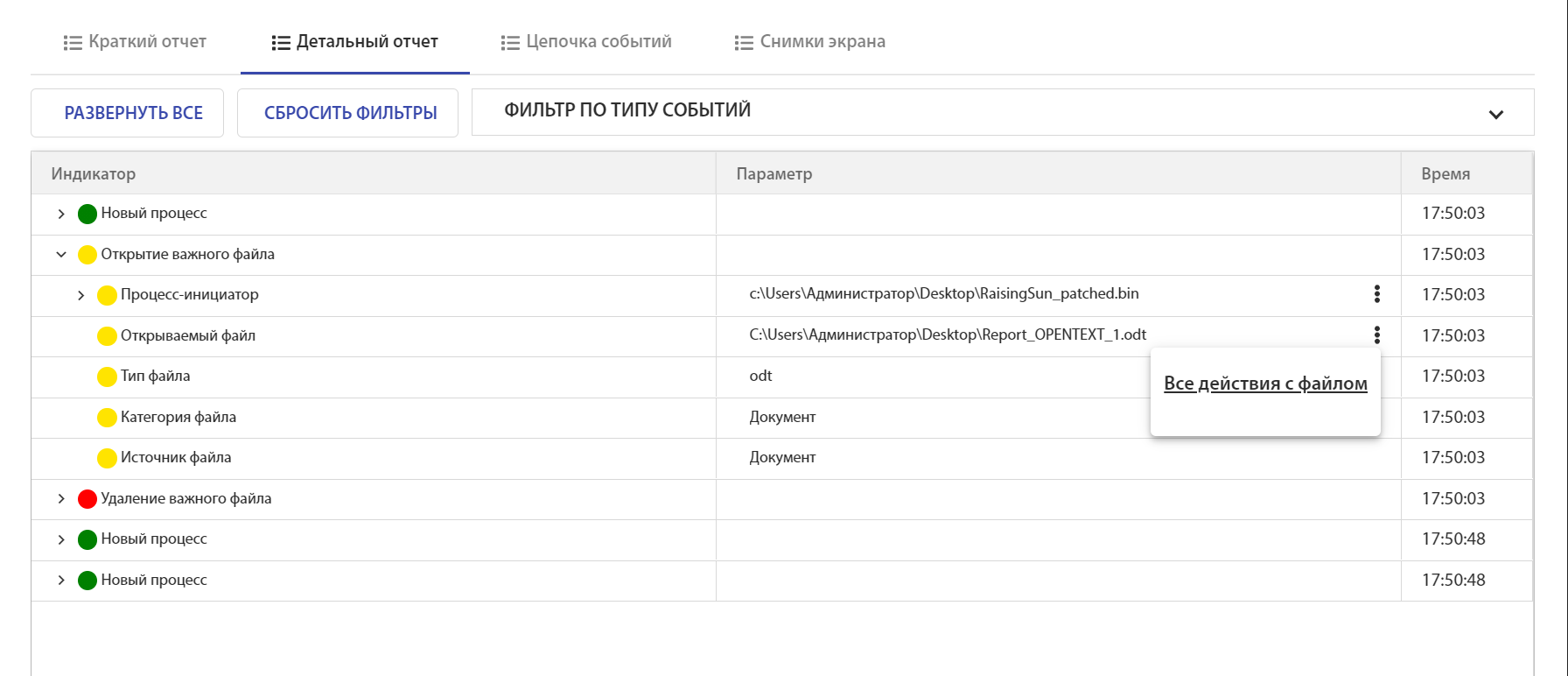
0x78005D008B00C6 C:\Users\Администратор\Desktop\Report_OPENTEXT_1.odt
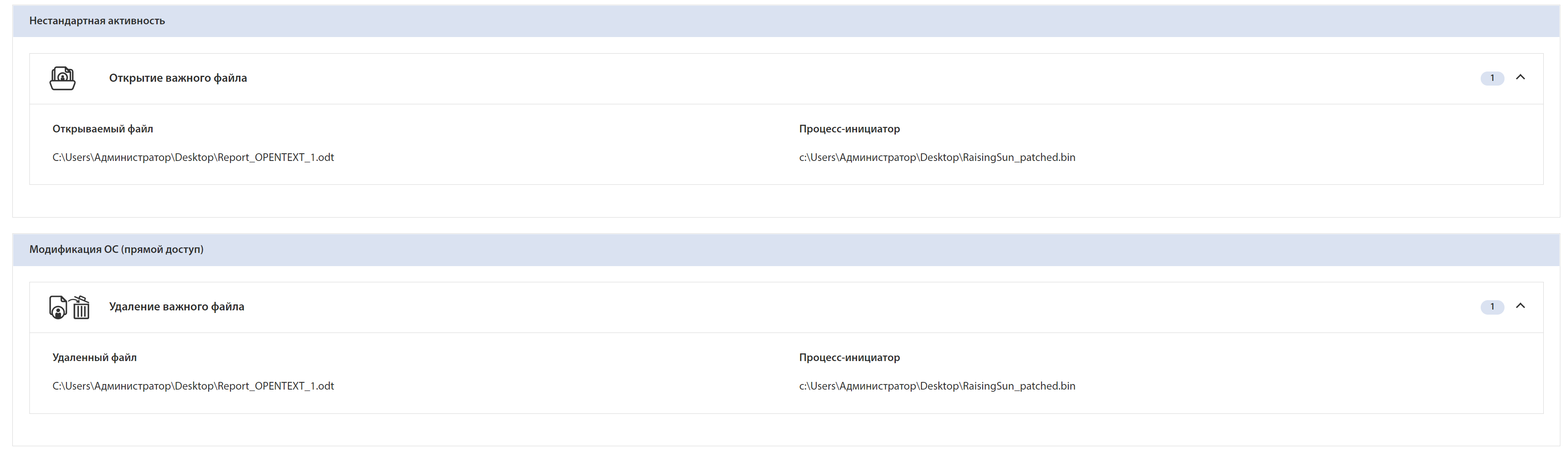
You can select a specific file and view actions with it:
Conclusion
The method of dynamic analysis of the Rising Sun sample in the tLab system was clearly shown using an implant developed by us that allows testing malware in the absence of active C&C servers.
